Introduction. Docker has transformed the way modern applications are built and deployed, but one of the most confusing parts for many developers is understanding how networking actually works inside Docker. When you launch containers, it’s easy to thi ...
Virtual Networks 101: Understanding Subnets, Gateways, and Routing.
Introduction. In the modern era of cloud computing, networks form the backbone of virtually every application and service, enabling resources to communicate, share data, and deliver functionality efficiently and securely. As organizations migrate to c ...
What Is HashiCorp and Why DevOps Teams Love It?
Introduction. Infrastructure as Code has fundamentally changed the way organizations build, deploy, and manage modern IT infrastructure, enabling teams to automate complex workflows, reduce human error, and achieve consistency across environments. Amo ...
Provision a Linux VM on a cloud provider.
Introduction. Infrastructure as Code (IaC) has become an essential practice in modern cloud computing, allowing teams to automate, standardize, and scale their environments with minimal manual intervention. Terraform, a powerful and provider-agnostic ...
10 Common VirtualBox Errors and How to Fix Them.
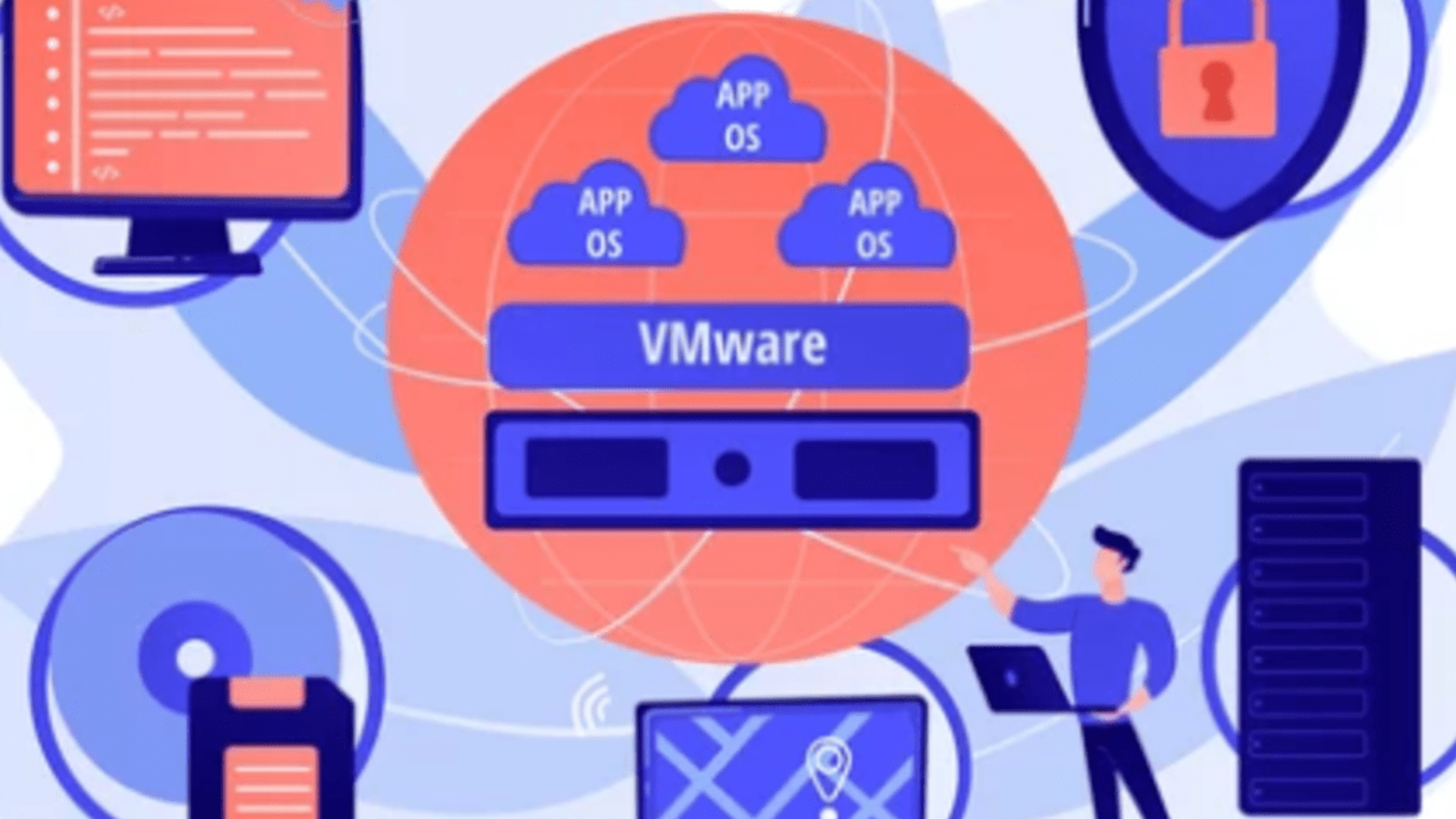
Introduction. VirtualBox has become one of the most widely used virtualization tools for running multiple operating systems on a single computer. For beginners and professionals alike, it provides a powerful, flexible, and cost-free way to explore tec ...
Understanding Virtualization: Why VirtualBox Is Perfect for Beginners.
Introduction. Virtualization has become one of the most important concepts in modern computing, shaping the way people learn, test, and interact with technology. As digital tools continue to evolve, the need for safe, flexible, and accessible learning ...
What Is VirtualBox? A Complete Beginner’s Guide.
Introduction. VirtualBox has become one of the most widely used tools for virtualization, offering a simple yet powerful way to run multiple operating systems on a single computer.In a world where learning, testing, and experimenting with technology h ...
Why Python Is the Most Popular Language in DevOps.
Introduction. Python has quickly become the backbone of modern DevOps practices, emerging as the go-to language for automation, cloud operations, CI/CD pipelines, and large-scale infrastructure management.As DevOps transforms how organizations build, ...
Python for Absolute Beginners: A 30-day learning roadmap.
Introduction. Python has become one of the most popular and beginner-friendly programming languages in the world,thanks to its simple syntax and wide range of real-world applications.Whether you're interested in data science, web development, automati ...
What Is Subnetting? A Non-Technical Explanation for Absolute Beginners.
Introduction. Networking can feel intimidating at first, especially when you start encountering terms like IP addresses, subnet masks, CIDR notation, and of course, subnetting. Many beginners immediately assume subnetting is a complicated math problem ...