Introduction.
In today’s digital landscape, security is paramount—especially when exposing APIs that serve as the backbone of mobile, web, and microservices-based applications. AWS offers a robust solution for managing API access and securing endpoints using Amazon API Gateway in conjunction with Amazon Cognito User Pools. This guide walks you step-by-step through the process of integrating these two powerful services to implement user authentication and authorization, enabling you to protect your APIs effectively. Amazon Cognito User Pools serve as a user directory that can manage sign-up and sign-in services for your applications, making it a convenient and secure way to manage identity in the AWS ecosystem. API Gateway, on the other hand, acts as a front door to your backend services, allowing you to control traffic, enforce throttling, and now—via Cognito—verify that incoming requests are from authenticated users.
When these services are used together, they provide a scalable and secure mechanism for ensuring that only valid users can access your resources. This integration means you no longer need to build and maintain your own user authentication system, reducing development overhead and security risk. In this tutorial, we will go from setting up a Cognito User Pool to creating and securing an API Gateway endpoint. You’ll learn how to configure the user pool, set up a test user, and link your API Gateway to require valid JWT tokens issued by Cognito. We’ll cover key concepts like identity tokens, authorizers, scopes, and OAuth 2.0 flows. Whether you’re developing a serverless application, a REST API, or a backend for your mobile app, securing it with Cognito and API Gateway ensures only authenticated users can interact with your services.
We will also walk through testing the integration using tools like Postman and AWS CLI, debugging common errors, and managing user permissions using Cognito groups. Additionally, you’ll understand how to configure token expiration and refresh, to keep your user experience seamless while maintaining robust security. By the end of this guide, you’ll have a working example of a secure API that authenticates users via Cognito, issues tokens, and validates those tokens before granting access to your API. This method is not only secure but also aligns well with modern cloud-native design principles, ensuring your architecture is both resilient and scalable. Whether you’re new to AWS or an experienced developer, this step-by-step walkthrough will give you a practical foundation for implementing secure, authenticated API access using AWS services. Let’s dive in and start building a secure API gateway with Cognito User Pools.

1. Create a Cognito User Pool
- Go to the Cognito console.
- Choose “Create user pool”.
- Configure the settings:
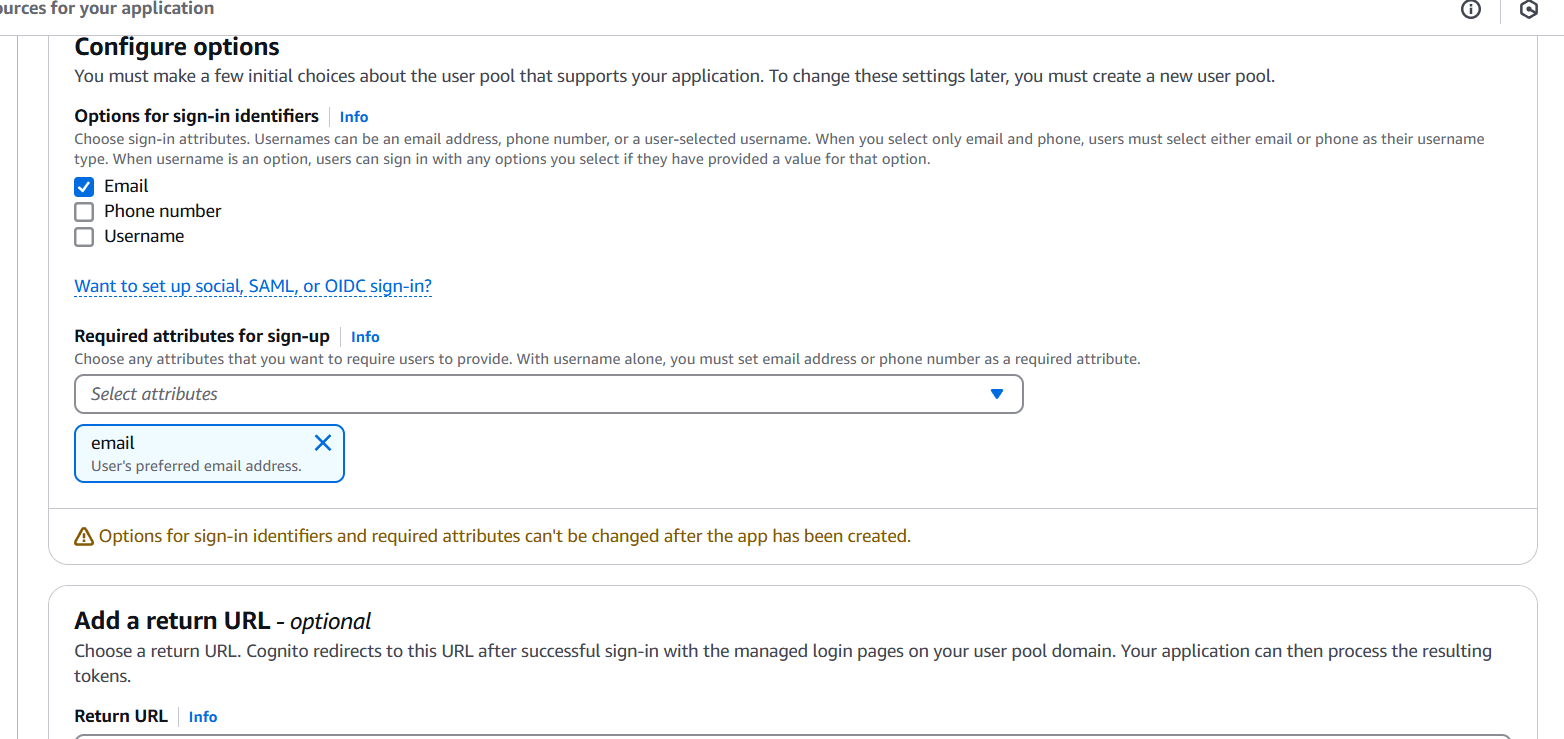
- Pool name, password policy, sign-in options (e.g., email, username).
- Create an App Client (no client secret required if using JavaScript).
- Note the User Pool ID and App Client ID.

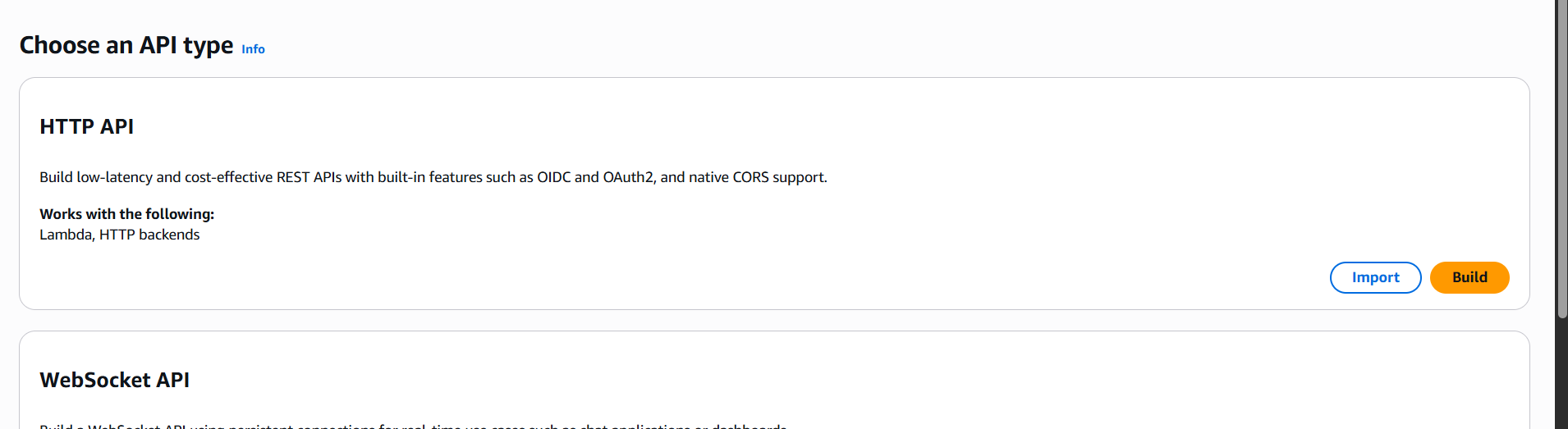
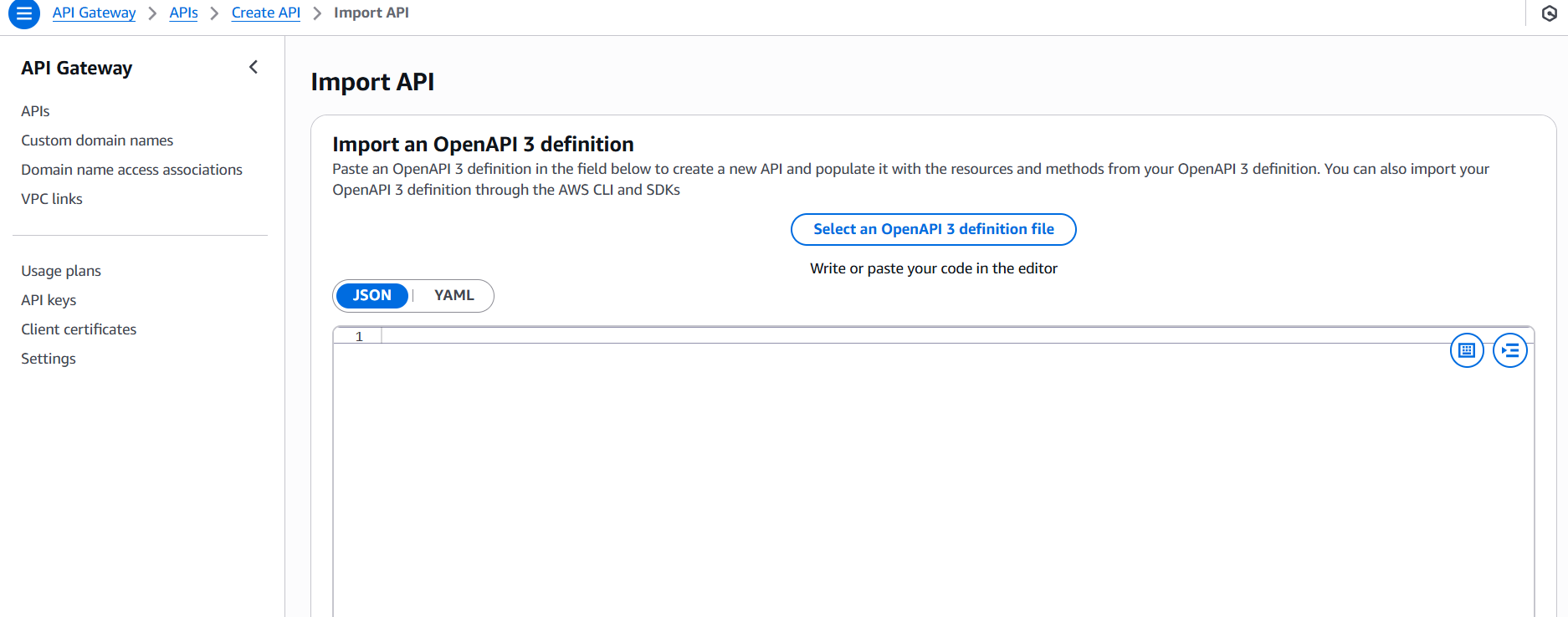
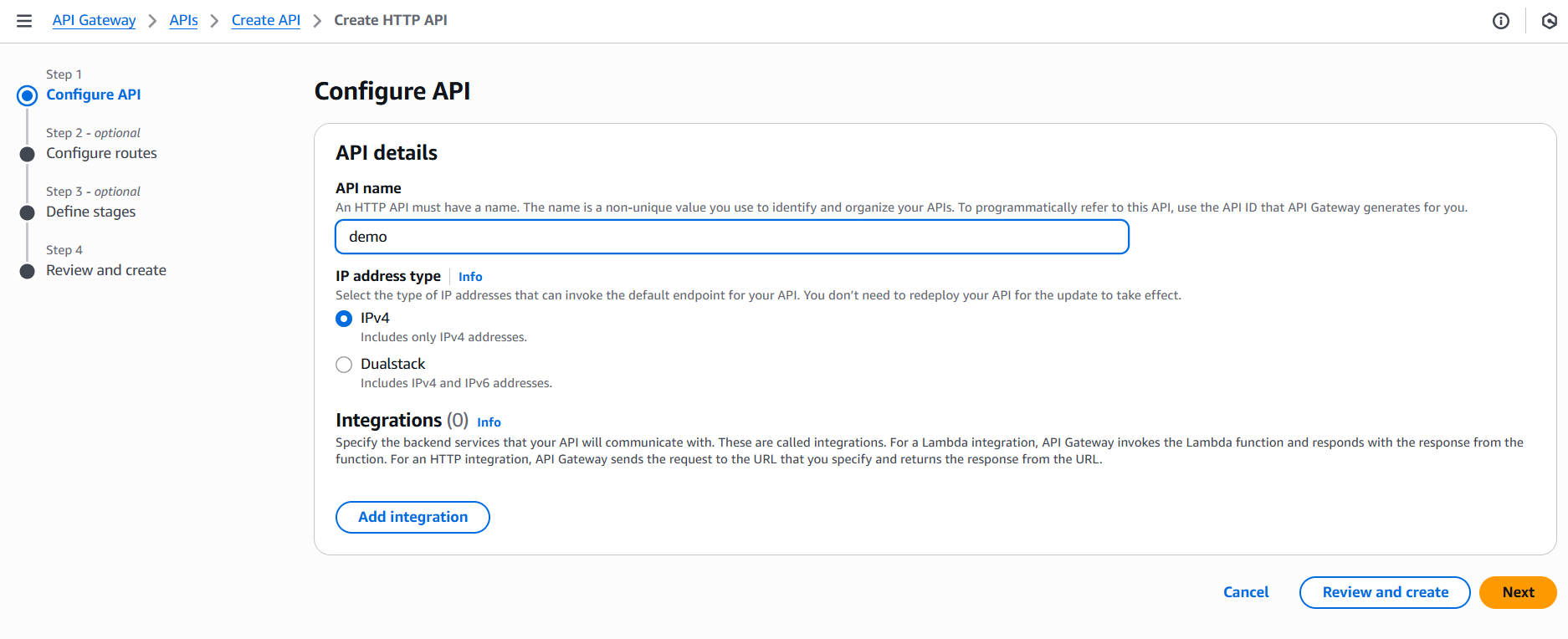
2. Create an API in API Gateway
- Go to the API Gateway console.
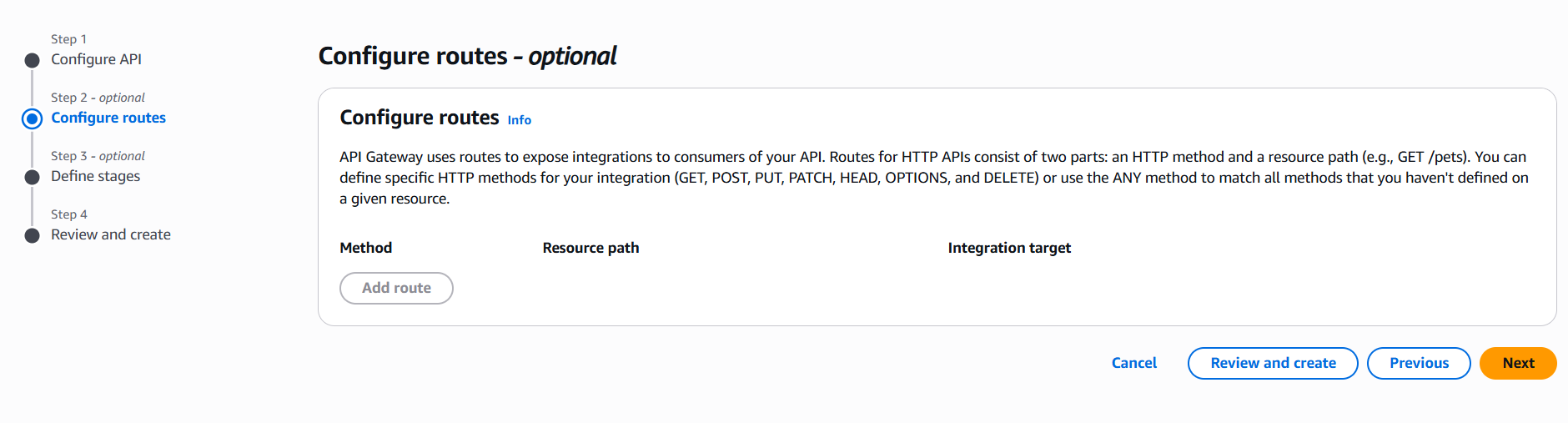
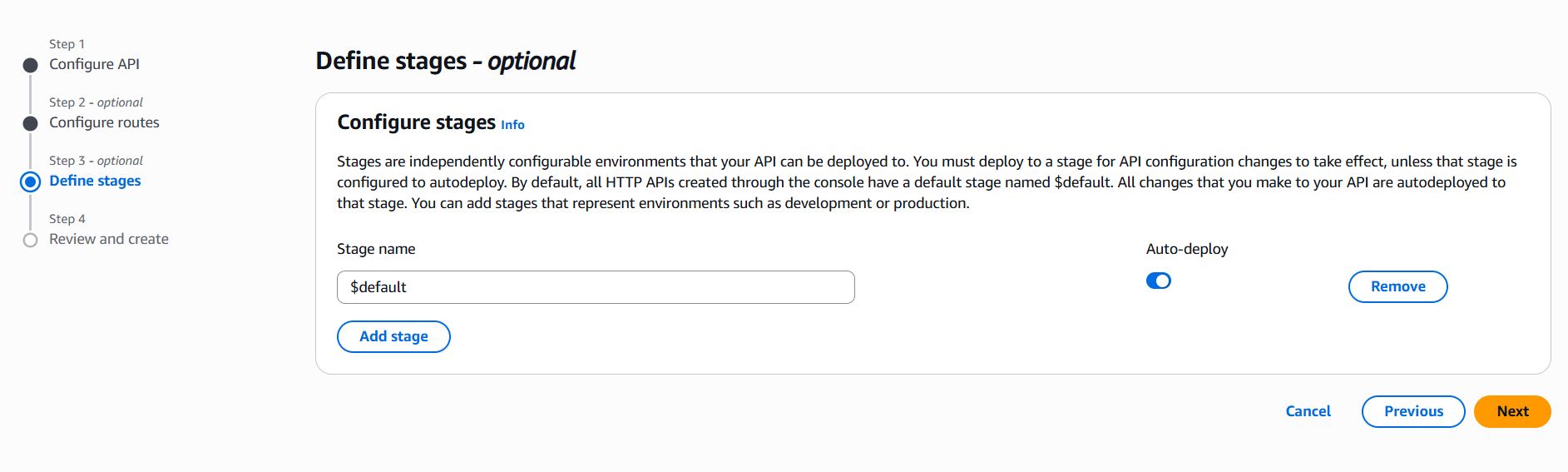
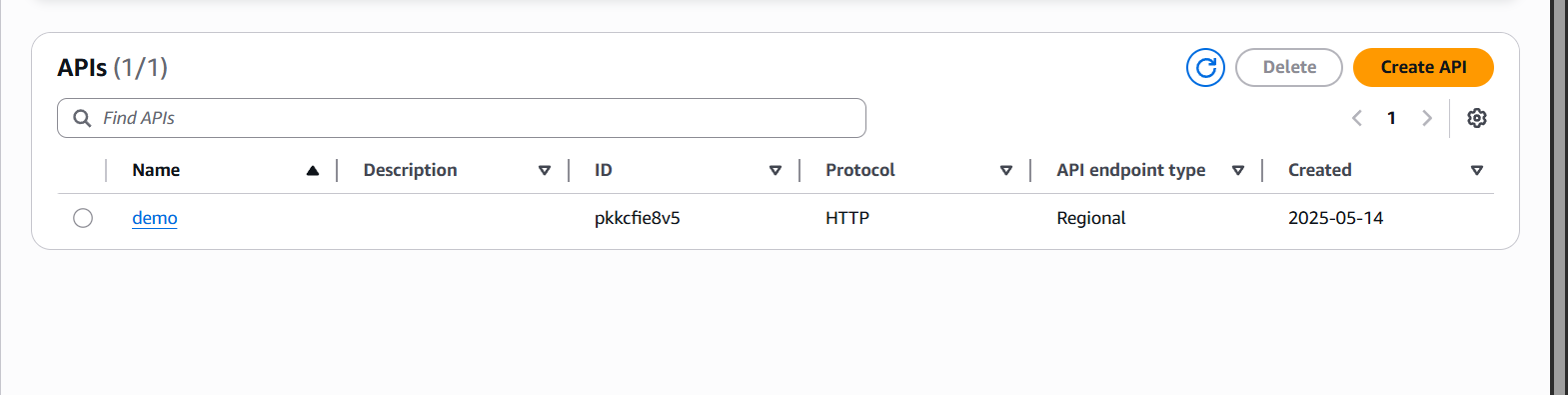
- Choose Create API → HTTP API or REST API.
- Configure your routes and integration (Lambda, HTTP backend, etc.).
3. Add an Authorizer
For HTTP APIs:
- Under your API, go to “Authorization”.
- Choose “Add authorizer” → Select Cognito.
- Enter:
- A name for the authorizer.
- Select your Cognito User Pool and App Client.
- Enable JWT token validation using the issuer URL:
https://cognito-idp.<region>.amazonaws.com/<userPoolId>
For REST APIs:
- Go to Authorizers → Create new authorizer.
- Choose type: Cognito.
- Enter:
- Name, Cognito User Pool, and Token Source (usually
Authorizationheader).
- Name, Cognito User Pool, and Token Source (usually
- Save the authorizer.
4. Secure Your Routes
- For HTTP APIs:
- Go to Routes → select the route.
- Under Authorization, select your Cognito authorizer.
- For REST APIs:
- Go to your Method Request → Enable Authorization → Select the Cognito Authorizer.


5. Test Authentication
- Use AWS Amplify or Cognito SDK to sign in a user and get a JWT token.
- Send an HTTP request to your API Gateway with the token:
GET /your-api-endpoint
Host: your-api-id.execute-api.region.amazonaws.com
Authorization: eyJraWQiOiJrZXlfaWQiLCJhbGciOi...

Conclusion.
Securing your APIs is no longer a luxury—it’s a necessity. By integrating Amazon API Gateway with Cognito User Pools, you’ve learned how to implement a secure and scalable authentication mechanism that protects your backend services from unauthorized access. This approach leverages AWS-managed identity services, reducing the complexity of building and maintaining your own user management and token validation systems. Through this step-by-step process, you configured a Cognito User Pool, created and tested a user, established an API Gateway with a Cognito authorizer, and verified token-based access control. You’ve seen how this setup not only enhances security but also supports modern authentication flows such as OAuth 2.0 and JWT, making it ideal for both web and mobile applications. As your application grows, you can build on this foundation—adding features like multi-factor authentication (MFA), custom user attributes, and fine-grained access control using Cognito groups and IAM roles. In adopting this solution, you’re following best practices in cloud security and creating a future-proof API infrastructure. With your secure API in place, you’re now well-equipped to support user-authenticated, scalable, and compliant applications on AWS.
Add a Comment