Introduction.
In modern cloud architectures, scalability, control, and security are crucial pillars of network design. As organizations grow their cloud presence, they often end up managing multiple Amazon Virtual Private Clouds (VPCs), VPNs, and even direct connections across accounts and regions. This increasing complexity can quickly turn network management into a tangled mess—especially when trying to maintain visibility, enforce routing rules, or implement fine-grained traffic control. This is where AWS Transit Gateway enters the picture as a powerful service that simplifies connectivity and centralizes network routing. But to truly unlock its full potential, especially in scenarios that demand granular control over how traffic flows between connected attachments, you need to understand and leverage the Transit Gateway Policy Table feature.
Transit Gateway Policy Tables are a relatively recent enhancement that allow you to apply route-based decisions based on source, destination, and type of attachment. Unlike the traditional route tables that direct traffic based on destination IP ranges alone, policy tables offer a more intent-based routing mechanism. Think of them as an intelligent traffic cop within the Transit Gateway—allowing or denying traffic between attachments based on defined rules. This means you can now say things like: “Allow traffic from VPC A to VPC B, but only if it’s HTTP traffic,” or “Deny access from a VPN connection to our internal development environment.” These capabilities give cloud architects and security teams the kind of fine-tuned control that’s essential for multi-account, multi-VPC environments operating at scale.
In this guide, we’ll walk through the process of creating a Transit Gateway Policy Table from scratch. Whether you’re a cloud engineer just getting familiar with AWS networking or an experienced architect looking to tighten access control between environments, this tutorial will break down the setup into manageable steps. We’ll start by reviewing the prerequisites you’ll need—like an existing Transit Gateway—and the IAM permissions required to create and manage policy tables. From there, we’ll go step-by-step through creating the table, associating it with attachments, and defining custom policy rules.
We’ll also explore common use cases for Transit Gateway Policy Tables, such as isolating test and production environments, enforcing zero-trust principles, and simplifying compliance in regulated environments. By the end of this guide, you’ll understand not only how to set up a policy table but also how to use it effectively as part of a broader network security and management strategy.
AWS has continued to evolve its network services to keep up with the demands of modern enterprises, and Transit Gateway Policy Tables are a testament to that progress. They offer a level of control and visibility that was previously only achievable through complex workarounds or third-party solutions. Now, with just a few clicks—or commands in the AWS CLI—you can implement policies that help safeguard your cloud infrastructure while keeping it flexible and scalable.
So whether you’re managing a simple two-VPC setup or orchestrating a full-scale cloud backbone for a global enterprise, understanding how to use Transit Gateway Policy Tables is a skill worth mastering. Let’s dive into the details and get started on building one.

1. Prerequisites
- You need an AWS Transit Gateway already created.
- You must have the necessary IAM permissions (e.g.,
ec2:CreateTransitGatewayPolicyTable,ec2:AssociateTransitGatewayPolicyTable, etc.).
2. Using AWS Console
- Open the Amazon VPC console at https://console.aws.amazon.com/vpc/.
- In the navigation pane, choose Transit Gateway Policy Tables.
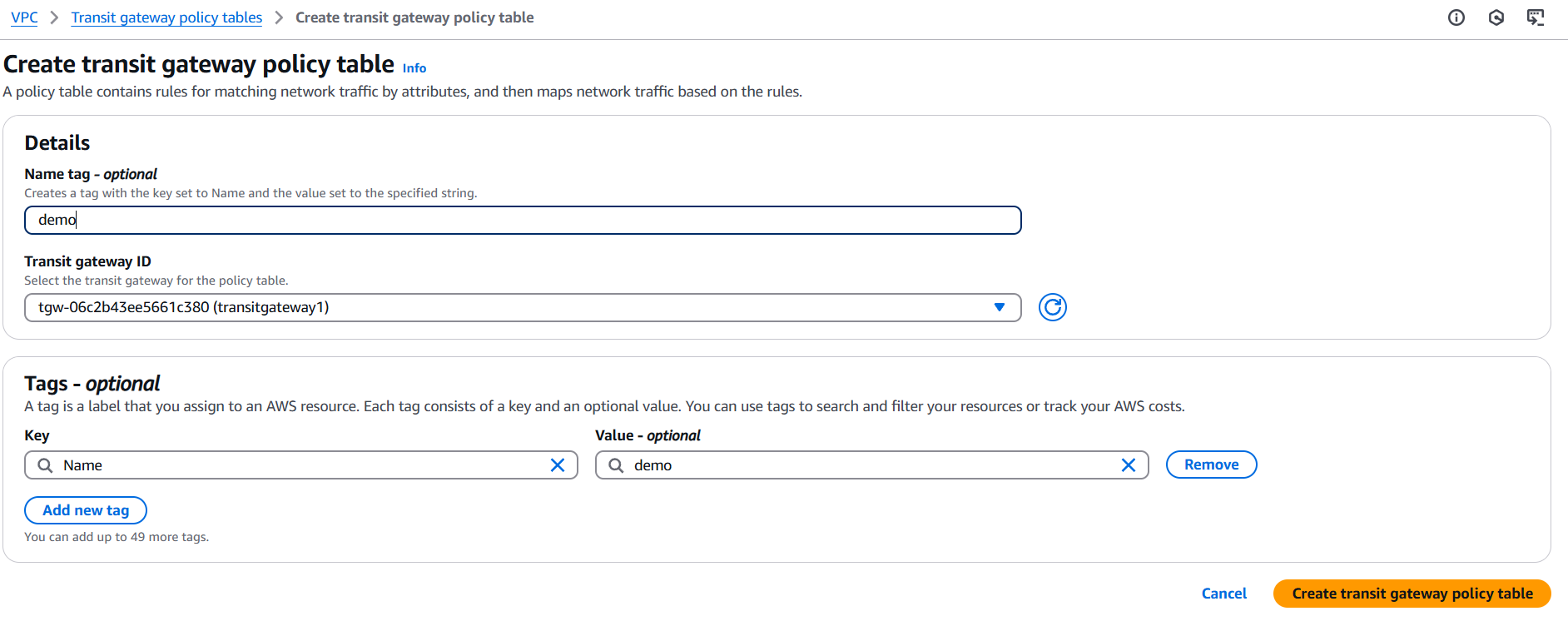
- Click Create Transit Gateway Policy Table.
- Fill out the following:
- Name tag – Optional name.
- Transit Gateway ID – Select the Transit Gateway.
- Click Create.
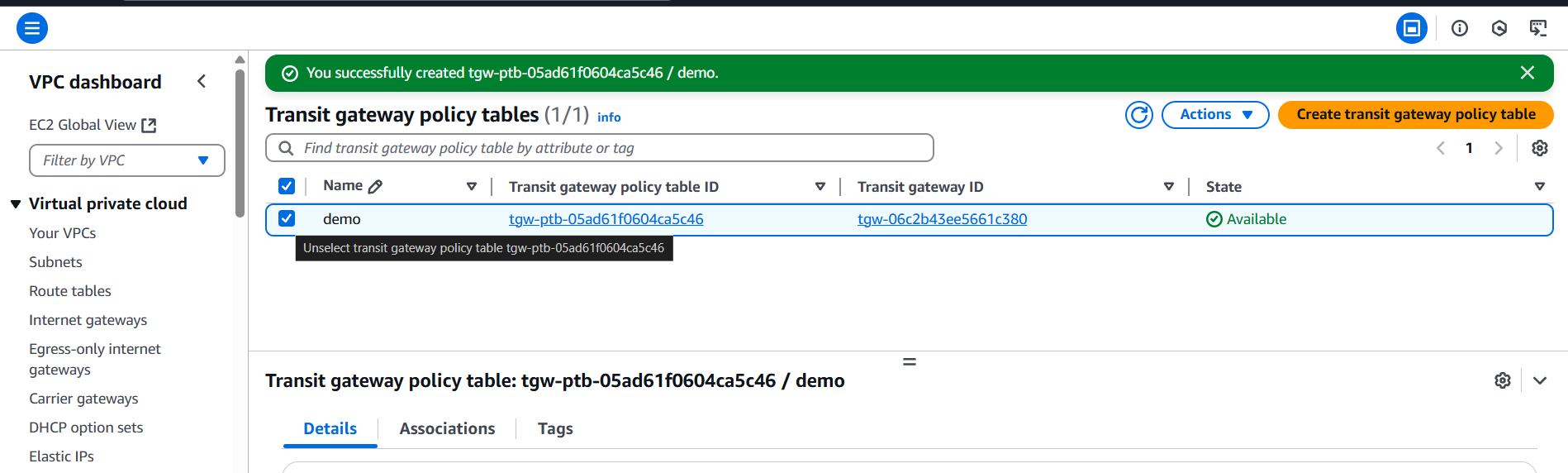
3. Associate Policy Table with Attachments
- In the Transit Gateway Policy Table list, select your newly created table.
- Choose the Associations tab.
- Click Create association.
- Select the attachments (VPCs, VPNs, etc.) that will use the policy table.
- Click Associate.
4. Define Policy Rules
- Go to the Policy Rules tab.
- Click Add Rule.
- Define:
- Source (CIDR, attachment, or resource type)
- Destination (CIDR, attachment, or resource type)
- Action (e.g.,
accept,deny) - Protocols, Ports (optional)
You can add multiple rules to customize traffic flow.
5. (Optional) Using AWS CLI
# Create a policy table
aws ec2 create-transit-gateway-policy-table \
--transit-gateway-id tgw-1234567890abcdef0
# Associate a policy table
aws ec2 associate-transit-gateway-policy-table \
--transit-gateway-policy-table-id tgw-ptb-abc123 \
--transit-gateway-attachment-id tgw-attach-xyz456
# Add a policy rule
aws ec2 modify-transit-gateway-policy-table \
--transit-gateway-policy-table-id tgw-ptb-abc123 \
--add-policy-rule '{
"SourceCidrBlock": "10.0.0.0/16",
"DestinationCidrBlock": "192.168.1.0/24",
"PolicyRuleAction": "accept"
}'Advantages.
1. Fine-Grained Traffic Control
Policy tables let you define rules based on source, destination, port, protocol, and attachment type, allowing precise control over traffic flows—something not possible with basic route tables.
2. Centralized Policy Management
You can manage traffic rules in one place across multiple VPCs, VPNs, and Direct Connect links, reducing complexity and making your infrastructure easier to audit and maintain.
3. Enhanced Security
By defining explicit “accept” or “deny” rules, you can enforce zero-trust networking models and reduce the attack surface between connected networks. This is especially useful in regulated environments.
4. Intent-Based Routing
Instead of manually managing routes based on CIDRs, policy tables allow logical routing based on intent, such as allowing “all traffic from Dev VPCs to reach the logging VPC” without needing complex subnet mappings.
5. Scalability Across Multi-Account Architectures
In AWS Organizations or Control Tower environments, Transit Gateway Policy Tables simplify managing traffic between accounts by applying rules consistently—no need for per-account route table micromanagement.
6. Environment Isolation
You can easily isolate environments (e.g., test, dev, prod) and enforce communication policies between them. For example, allowing test to reach dev, but not prod.
7. Auditability & Compliance
Policies are easier to document and review compared to sprawling route tables. This helps during compliance audits or when proving access control to security teams.
8. Visual and Logical Rule Management
Through the AWS Console or API, you can visually inspect and manage rules, making it easier to understand and troubleshoot network policies.
9. Integration with AWS CLI and SDKs
You can fully automate the creation and management of policy tables via Infrastructure as Code (IaC) tools like CloudFormation, Terraform, or the AWS CLI.
10. Better Operational Efficiency
Reducing the need for custom network appliances, NAT configurations, or third-party firewalls improves network performance and reduces cost and operational overhead.

Conclusion.
In today’s cloud-native and multi-account environments, managing traffic flow with precision is no longer a luxury—it’s a necessity. AWS Transit Gateway Policy Tables offer a powerful solution for organizations looking to scale securely and efficiently. By moving beyond the limitations of traditional route tables, policy tables allow you to define intent-driven, rule-based traffic control between VPCs, VPNs, and other network attachments—all from a centralized, manageable interface.
Through this guide, you’ve learned how to create a Transit Gateway Policy Table, associate it with attachments, and define granular rules that give you full control over network behavior. Whether you’re segmenting workloads, enforcing strict security boundaries, or simply aiming for better visibility and control across your cloud infrastructure, Transit Gateway Policy Tables provide the tools to do so with confidence.
As AWS continues to expand its networking features, mastering capabilities like policy tables positions your organization to adopt best practices, reduce risk, and streamline operations. By incorporating policy tables into your architecture, you’re not just building a network—you’re designing a secure, scalable, and future-ready cloud environment.
Now that you understand the concepts and steps involved, it’s time to apply them in your own AWS environment and take full advantage of what Transit Gateway Policy Tables have to offer.

Add a Comment