Introduction.
In today’s cloud-driven world, managing access to resources securely and efficiently is non-negotiable. As organizations scale, the need for robust identity management becomes more critical, especially when multiple users, teams, and external systems require access to cloud infrastructure. That’s where AWS IAM Identity Providers come into play. An IAM Identity Provider acts as a bridge between AWS and your external identity system, enabling you to grant secure, temporary access to AWS resources without managing individual IAM users or hardcoded credentials. Whether you’re using a corporate SSO solution like Okta or Azure AD, implementing federated access with SAML, or connecting a modern identity platform like Google or GitHub via OIDC, IAM Identity Providers allow seamless integration with AWS’s powerful access control features.
Traditionally, many developers relied on long-term IAM credentials, which, although functional, come with security risks and management overhead. IAM Identity Providers offer a better alternative—by allowing you to define trust relationships, create short-lived sessions, and offload authentication to systems you already use. Imagine letting a developer in your company log in to the AWS Console with their existing company email, or enabling GitHub Actions to assume a role in your AWS account securely during a deployment. That’s the power of federated access through IAM Identity Providers.
Setting up an identity provider in AWS involves creating a trust relationship between your AWS account and your chosen external identity system. You then define IAM roles that specify who can assume them and what actions they can perform once authenticated. Depending on the provider type—SAML 2.0 for enterprise-grade federated access or OIDC (OpenID Connect) for modern, web-based identity platforms—the configuration process varies slightly, but the concept remains the same: delegate authentication, and use IAM to control authorization.
In this blog post, we’ll break down exactly how IAM Identity Providers work, when to use SAML vs. OIDC, and walk you through real-world setup scenarios—from enabling SSO for your team to securing automation with GitHub Actions. We’ll also cover common pitfalls, best practices, and how to debug issues when they arise. By the end, you’ll have a clear understanding of how to harness IAM Identity Providers to simplify access management in your AWS environment, reduce security risk, and align your cloud access policies with your organization’s identity strategy.

1. Choose the Identity Provider Type
a) SAML 2.0
Used for enterprise federated access (e.g., Okta, ADFS, Azure AD)
b) OIDC (OpenID Connect)
Used for modern identity providers like Google, Auth0, or GitHub Actions.
2. Set Up the Identity Provider in IAM
SAML 2.0
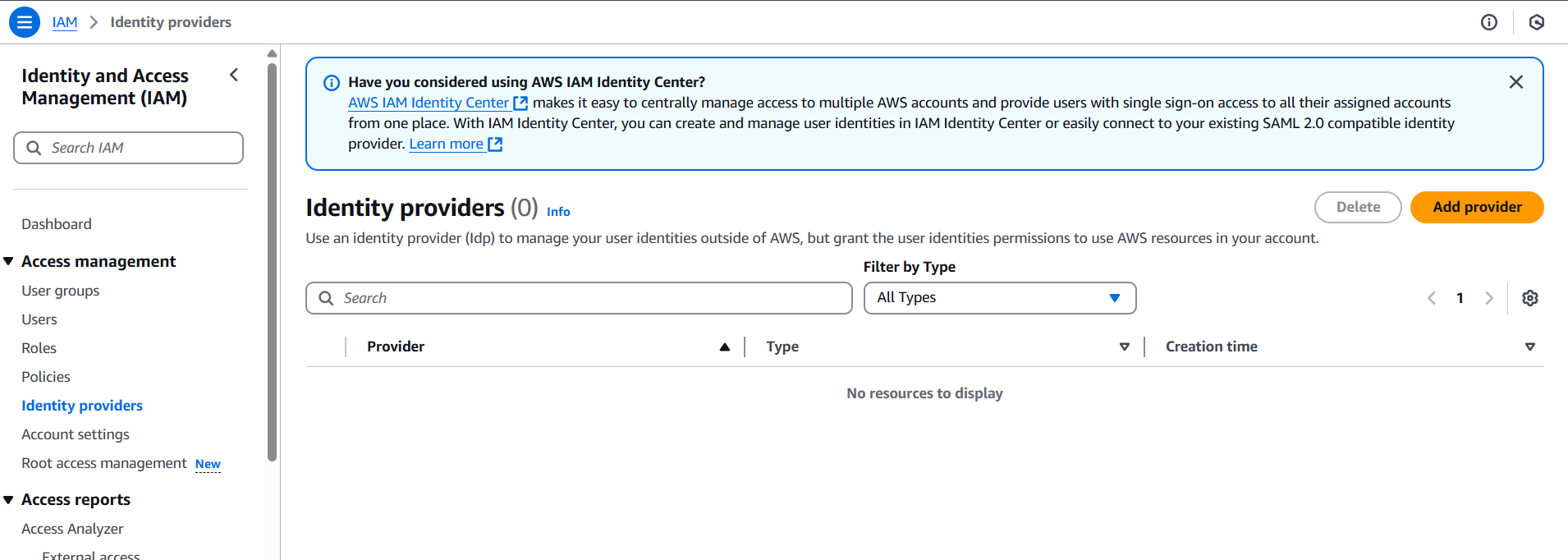
- In IAM → Identity providers → Add provider
- Choose SAML
- Enter a name (e.g.,
OktaProvider) - Upload your SAML metadata file (from your IdP)
- Create the provider
OIDC
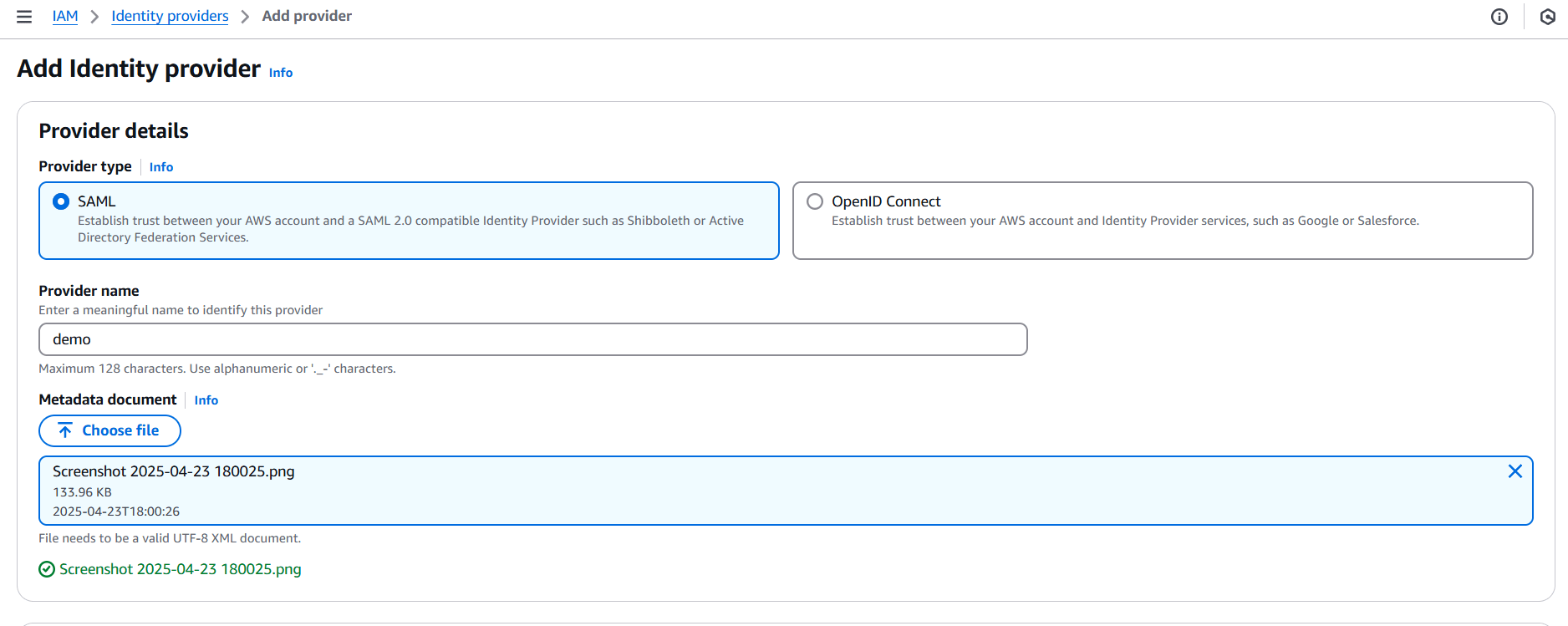
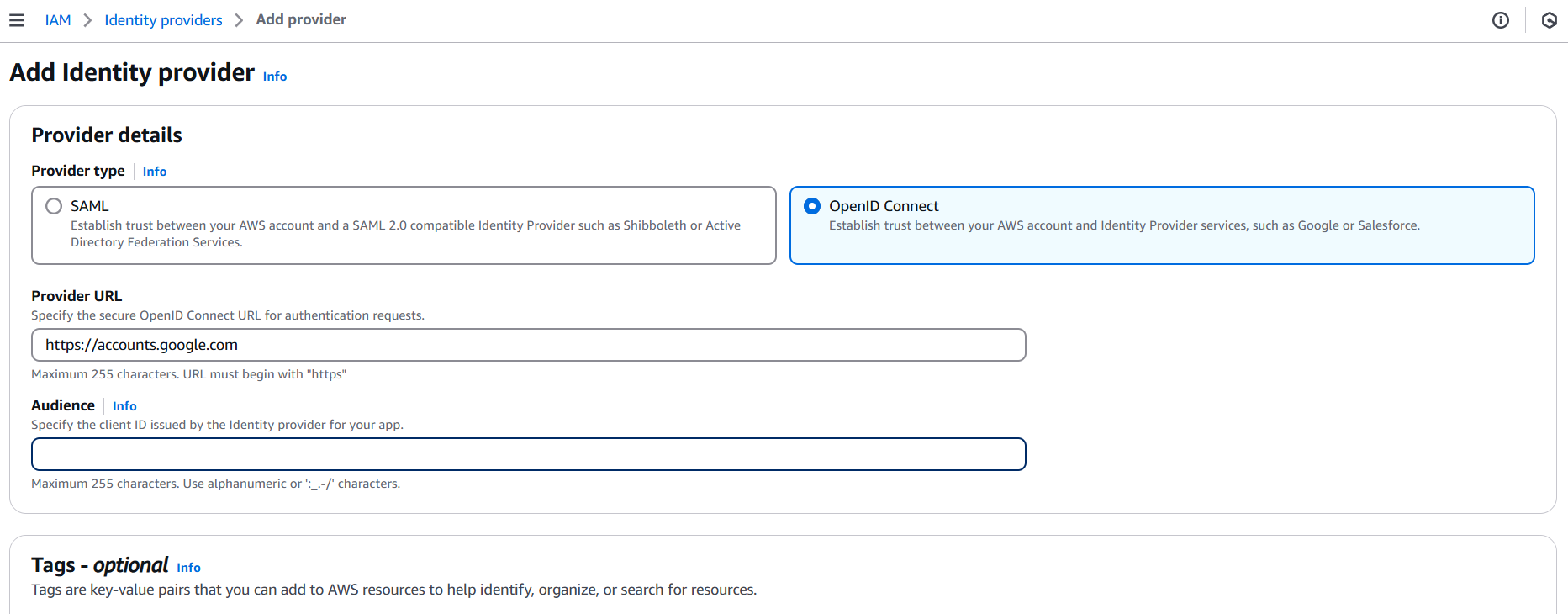
- IAM → Identity providers → Add provider
- Choose OIDC
- Enter your OIDC issuer URL (e.g.,
https://accounts.google.com) - Enter the client ID(s) and check the thumbprint (AWS will validate SSL)
- Create the provider
3. Create an IAM Role Trusted by the Identity Provider
- Go to IAM Roles → Create Role
- Select Web identity or SAML 2.0 federation depending on what you used
- Select the provider you created
- Choose the audience/client ID or SAML attributes that will assume the role
- Attach permissions (like
AmazonS3ReadOnlyAccess) - Give the role a name (e.g.,
FederatedUserRead only)

Conclusion.
In a world where secure, scalable, and flexible access control is critical, IAM Identity Providers in AWS offer a modern and efficient way to manage user authentication and authorization. By integrating external identity systems—whether enterprise-grade SAML providers or modern OIDC platforms—you can eliminate the need for long-term credentials, streamline user access, and enforce fine-grained permissions with IAM roles. This approach not only boosts your security posture but also simplifies access management across development teams, CI/CD pipelines, and third-party services. Whether you’re enabling SSO for your workforce or securing automated deployments, leveraging IAM Identity Providers gives you the best of both worlds: centralized identity management and AWS-native security controls. As you move forward, remember to align your configurations with best practices, audit roles and permissions regularly, and keep learning—because in the cloud, identity is the new perimeter.

Add a Comment