Introduction.
In the world of cloud infrastructure, security and controlled connectivity are crucial. Whether you’re building a web application, a data processing pipeline, or a backend service, the ability to manage how your resources communicate with the outside world is essential.
Amazon Web Services (AWS) offers a range of tools to architect your network securely and efficiently. One of the most important components in this toolkit is the NAT Gateway.
But what is a NAT Gateway, and why do you need one?
When you launch resources inside a private subnet in your Virtual Private Cloud (VPC), those resources don’t have direct access to the internet by default. This is a security feature—it prevents inbound traffic from reaching your private instances.
However, there are many scenarios where these private resources do need to access the internet. For example:
- Installing OS updates on an EC2 instance
- Pulling packages from online repositories (like
yum,apt,pip, ornpm) - Uploading logs to Amazon S3
- Downloading configuration files from remote servers
This is where the NAT Gateway comes in.
A NAT (Network Address Translation) Gateway allows instances in a private subnet to initiate outbound connections to the internet, while blocking inbound connections initiated from outside. This ensures a secure yet functional environment for your cloud resources.
In this guide, we’ll walk through:
- What a NAT Gateway is and how it works
- The prerequisites you need to set one up
- Step-by-step instructions to create a NAT Gateway using the AWS Console and CLI
- How to route private subnet traffic through your NAT Gateway
- Key considerations like cost, availability, and security best practices
Whether you’re a beginner exploring AWS networking for the first time, or an experienced cloud architect refining your VPC setup, this guide will help you set up a NAT Gateway confidently and correctly.
By the end, you’ll have a solid understanding of how to:
- Keep your instances protected in private subnets
- Allow them secure access to external services
- Ensure your AWS architecture meets best practices for both performance and security

Let’s get started by exploring the building blocks you’ll need before deploying your NAT.
1. Allocate an Elastic IP
- Go to the VPC Dashboard → Elastic IPs
- Click Allocate Elastic IP address
- Choose your scope (EC2 or VPC) and click Allocate
2. Create the NAT Gateway
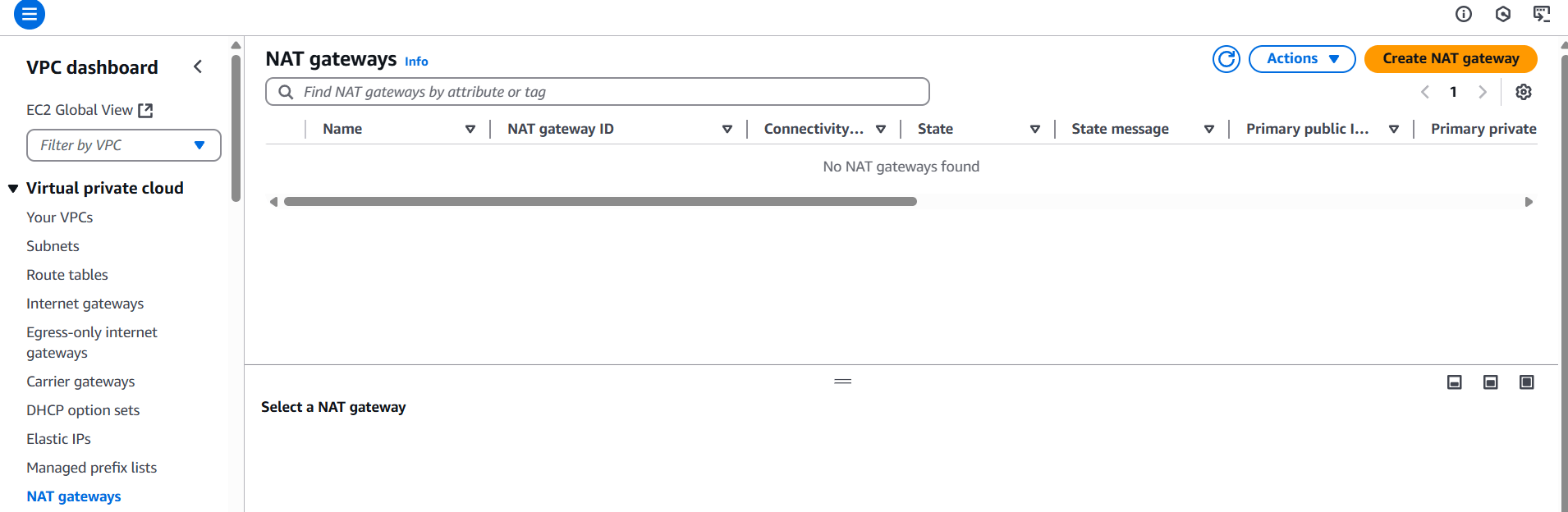
- Go to VPC Dashboard → NAT Gateways
- Click Create NAT Gateway
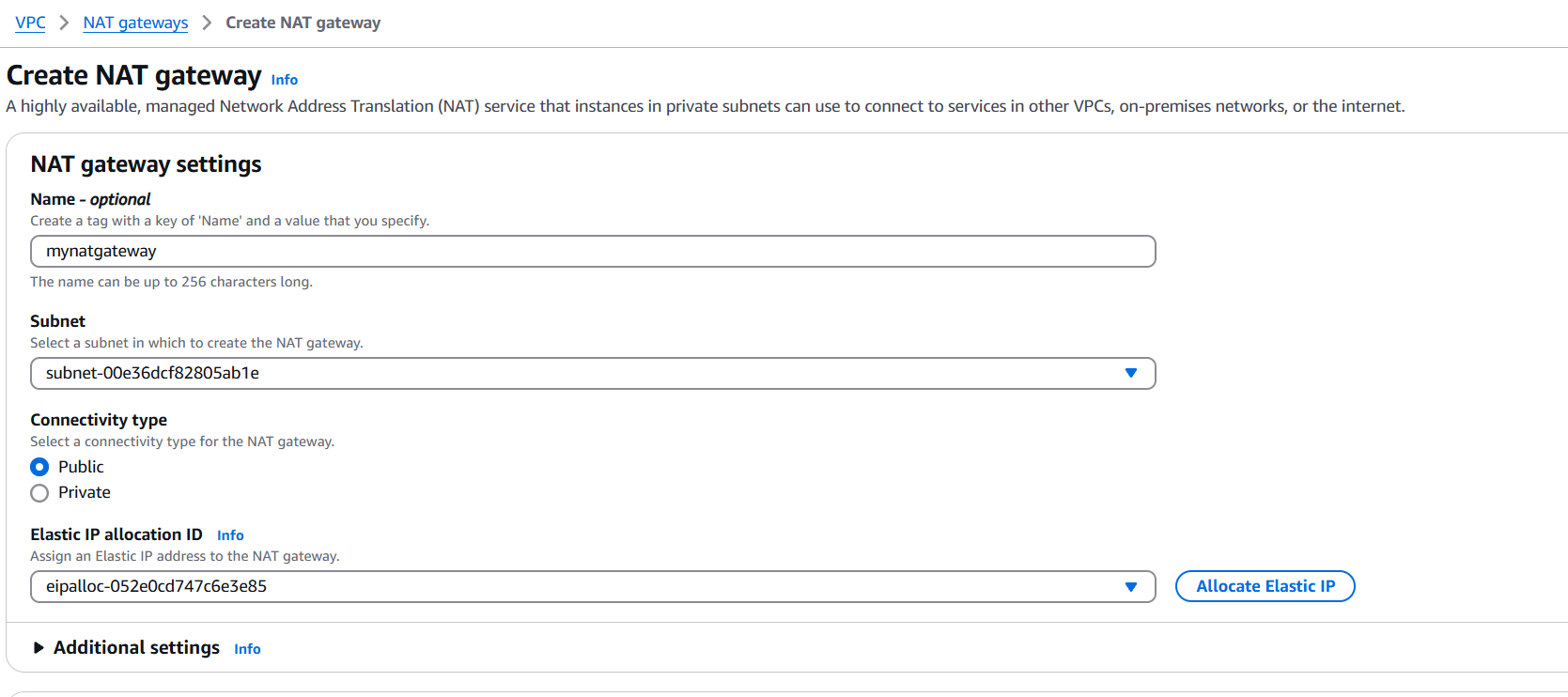
- Choose:
- Subnet: Must be in a public subnet (i.e., has a route to an Internet Gateway)
- Elastic IP: Use the one you just allocated
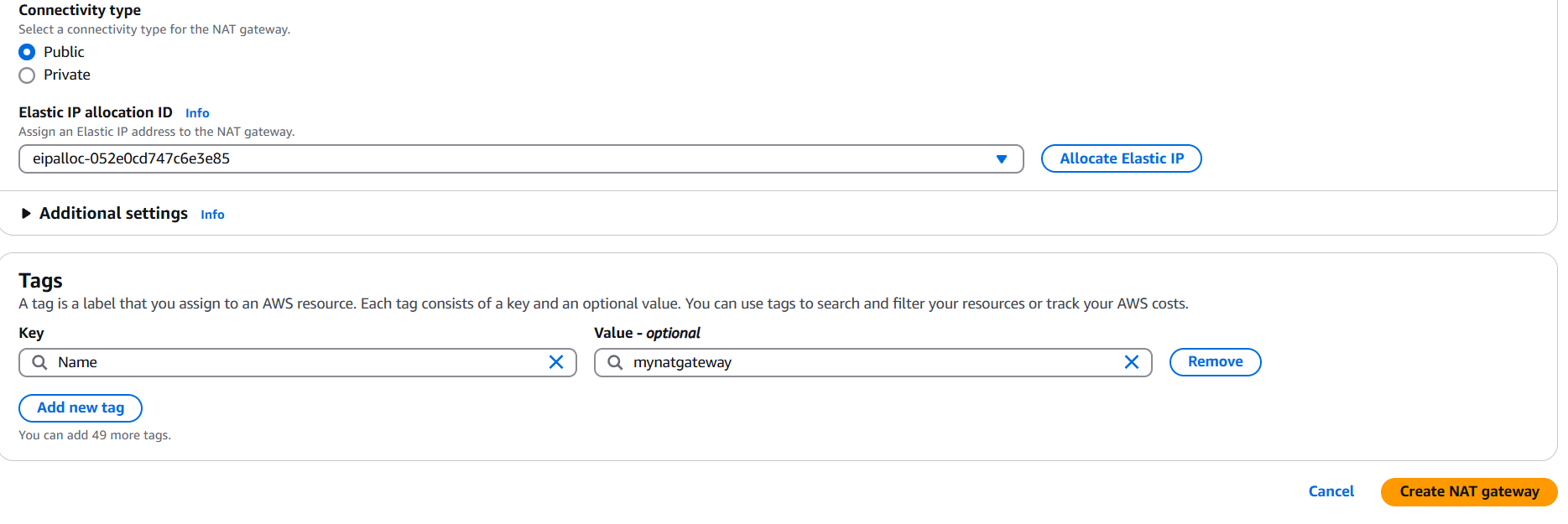
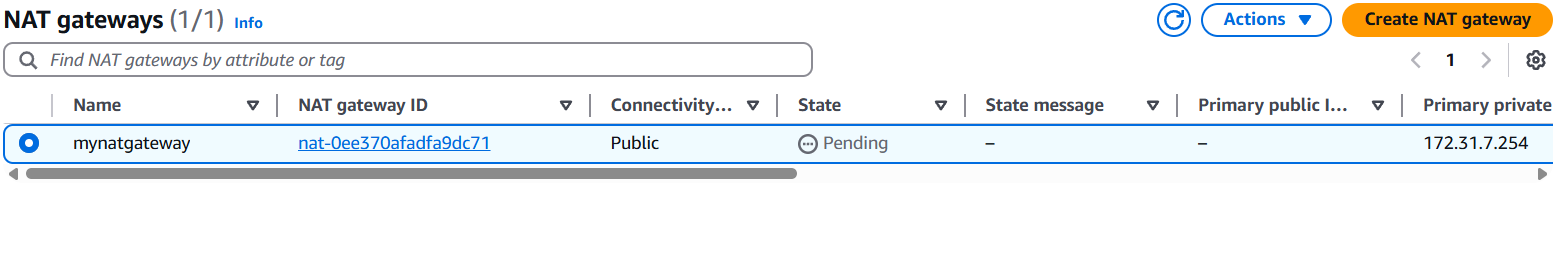
- Click Create NAT Gateway
3. Update Route Table for the Private Subnet
- Go to Route Tables
- Find the route table associated with your private subnet
- Click Edit routes → Add route:
- Destination:
0.0.0.0/0 - Target: your new NAT Gateway ID
- Destination:
- Save the route

Conclusion.
Setting up a NAT Gateway might seem like just another networking task in AWS, but it plays a vital role in designing secure, functional cloud environments. It gives your private subnet resources the ability to connect to the internet—without exposing them to unsolicited inbound traffic.
In this guide, we covered:
- What a NAT Gateway is and why it’s important
- How to allocate an Elastic IP and place the NAT Gateway in a public subnet
- How to route private subnet traffic through it using route tables
- How to automate the setup using the AWS Console or CLI
By implementing a NAT Gateway correctly, you ensure that your internal services remain protected behind a layer of network security, while still maintaining the internet access they need to function efficiently.
Keep in mind:
- NAT Gateways are zonal—consider multiple NAT Gateways for high availability across AZs
- There are usage costs—monitor data transfer and hourly charges
- Regularly review your route tables and VPC configuration for consistency and security
Whether you’re building a simple web app or scaling a multi-tier architecture, mastering NAT Gateway configuration is a fundamental AWS skill.
Ready to take your VPC setup to the next level? Try pairing NAT Gateways with other networking best practices like VPC Peering, Transit Gateways, and custom NACLs.

Add a Comment