Introduction.
Jenkins is a popular open-source automation server used to automate the process of building, testing, and deploying software. Since Jenkins is often used in continuous integration/continuous delivery (CI/CD) pipelines, ensuring its security is crucial to avoid potential risks like unauthorized access to sensitive information, codebase tampering, or pipeline manipulation. Here are some important security concepts in Jenkins:

Authentication
- Jenkins User Authentication: Jenkins provides user authentication using several methods such as its internal user database, LDAP, Active Directory, or OAuth integration.
- Matrix-based Security: This allows fine-grained control over who has access to different parts of Jenkins. You can specify which users or groups have permissions like “read,” “build,” “admin,” etc.
- LDAP Authentication: Many organizations use LDAP to authenticate users so that Jenkins can integrate with their existing user management systems.
Authorization
- Role-Based Access Control (RBAC): You can configure role-based access to define who has access to what within Jenkins. RBAC allows the segregation of duties, preventing unauthorized users from accessing or modifying critical resources.
- Matrix Authorization Strategy: It offers a flexible way to control access by setting permissions for users and groups.
Security Realm
- The Security Realm is a Jenkins concept used to manage the identity of users. Jenkins supports various security realms such as Jenkins’ internal user database, LDAP, or other external authentication systems (OAuth, SSO).
Authorization Strategy
Project-based Matrix Authorization: This restricts permissions for specific jobs, not just the entire Jenkins instance, which adds an additional layer of security for sensitive projects.
Crowd or SSO: Jenkins supports using external identity management systems like Atlassian Crowd or single sign-on (SSO) integration for centralized user authentication.
Pipeline Security
Script Approval: Jenkins allows administrators to approve or block scripts running in the pipeline, such as Groovy scripts, which could potentially contain malicious code. Users need to explicitly approve certain scripts before they are allowed to run.
Secure Agents: If you use distributed agents (slave nodes), make sure to properly configure the agent security, ensuring that the master has secure communication with agents. The communication should also be encrypted using TLS.
Auditing and Logging
Audit Logging: Jenkins provides a way to track all changes and actions performed in the system, such as job execution, user login, or configuration changes. It’s critical for identifying any suspicious activities or unauthorized actions.
Access Logs: Jenkins logs can be reviewed to track who accessed the system, when, and what actions were performed.
Encryption
TLS/SSL Encryption: Jenkins supports enabling HTTPS for secure communication between users and the Jenkins master or between master and agents. This prevents eavesdropping on sensitive information such as credentials or pipeline outputs.
Secrets Management: Jenkins has a “Credentials Plugin” that helps manage secrets, such as API tokens or passwords, safely. These credentials can be stored in the Jenkins Credentials Store and used securely within jobs and pipelines.
Plugins Security
Plugin Management: Jenkins allows the installation of plugins, which can sometimes introduce security vulnerabilities if not regularly updated. It’s important to maintain and update plugins to the latest secure versions.
Plugin Permission: Plugins should be audited for security and configured to ensure that they don’t introduce vulnerabilities. Certain plugins may grant escalated privileges, so care should be taken when installing them.
Security Hardening
Disable Unnecessary Features: To reduce the attack surface, Jenkins administrators should disable features they don’t need (e.g., the Jenkins CLI or remote access API) to prevent unwanted access or malicious activities.
CSRF Protection: Jenkins includes Cross-Site Request Forgery (CSRF) protection, which helps prevent attackers from tricking authenticated users into performing actions on Jenkins without their consent.
Enable Security Settings: Features like “Enable security” in Jenkins should always be turned on, enforcing users to authenticate before using Jenkins.
Backup and Recovery
Regular backups should be scheduled for Jenkins configurations, including jobs, plugins, and credentials, so that you can restore your Jenkins instance in case of an attack or failure.
Requirement.
- Set up Jenkins in https://jeevisoft.com/blogs/2024/10/easy-guide-to-set-up-jenkins-on-ubuntu-aws-ec2-instance/ EC2 instance
STEP 1: Create a new user on jenkins.
- Go to Jenkins dashboard.
- Select manage Jenkins and click on security.
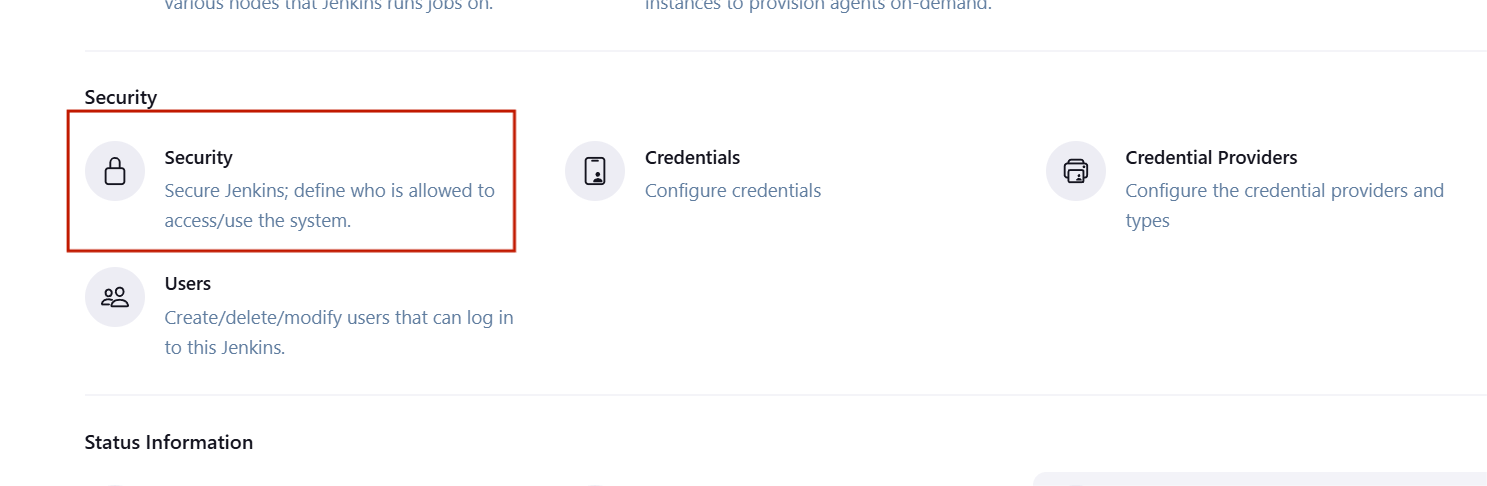
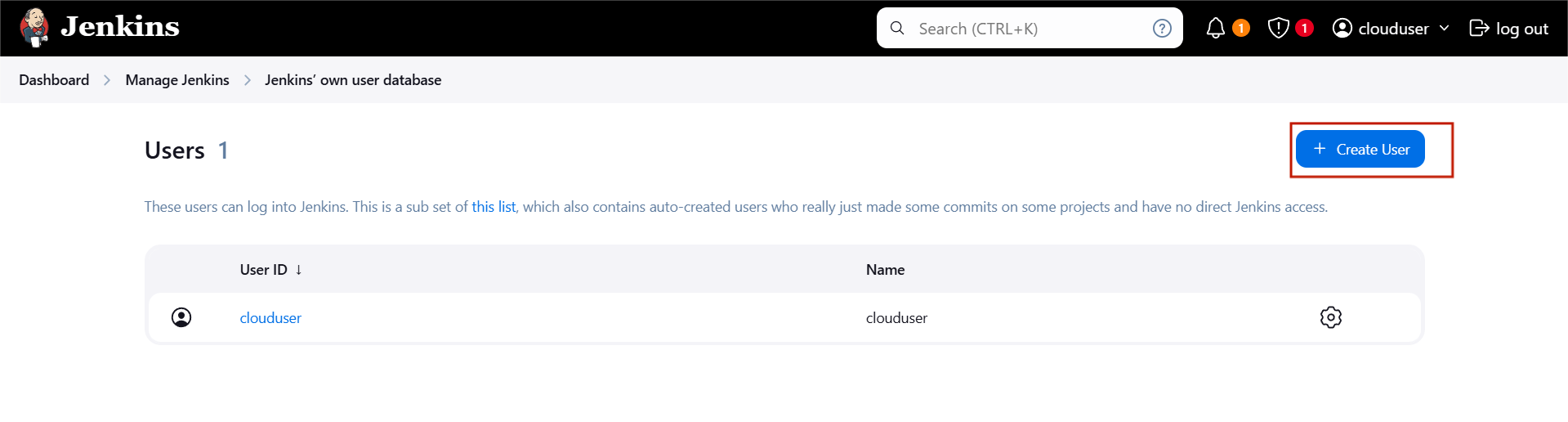
STEP 2: Click on create a user.
- Enter username, password, name and mail Id.
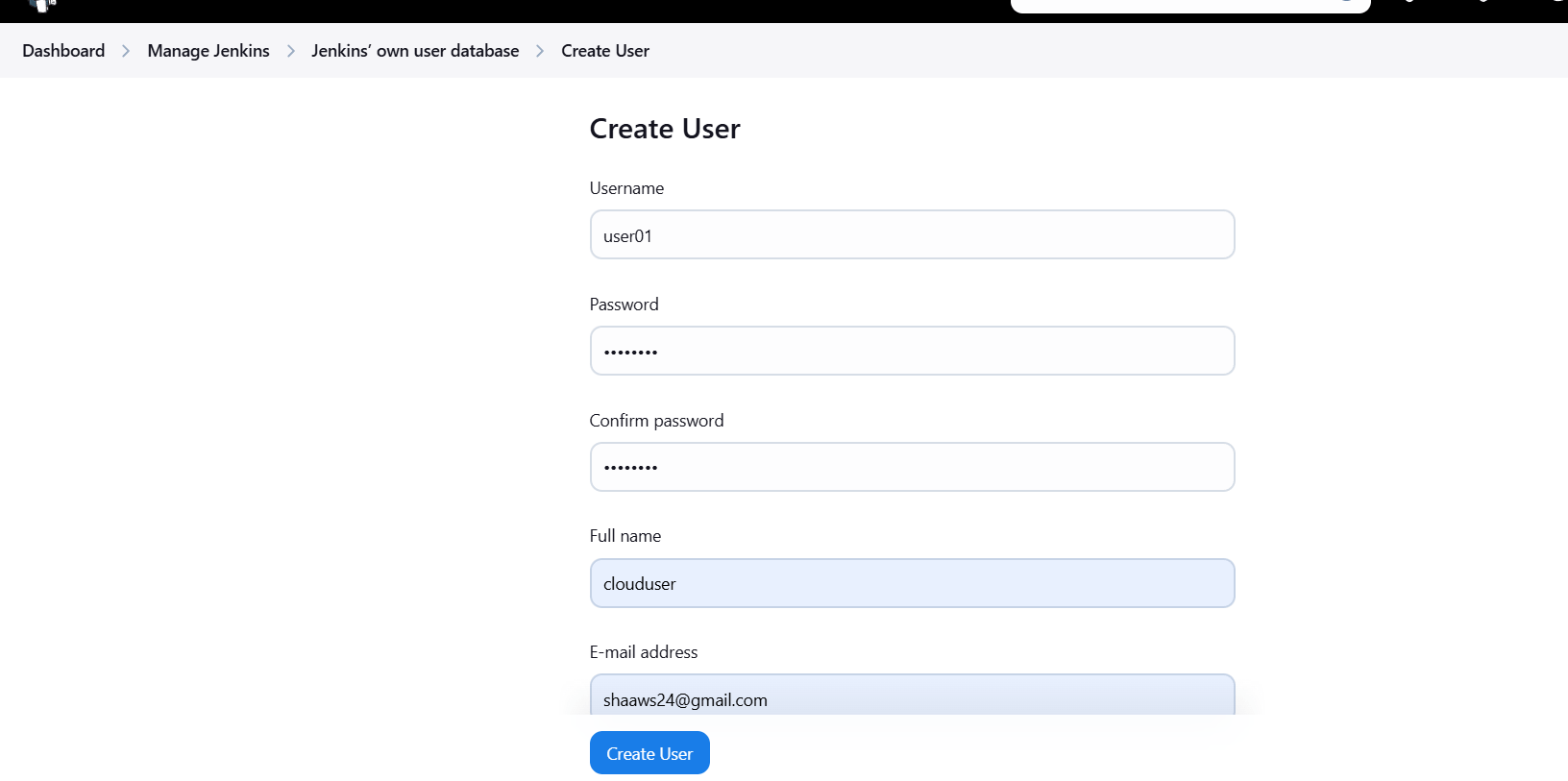
STEP 3: . You will see the user created by you.
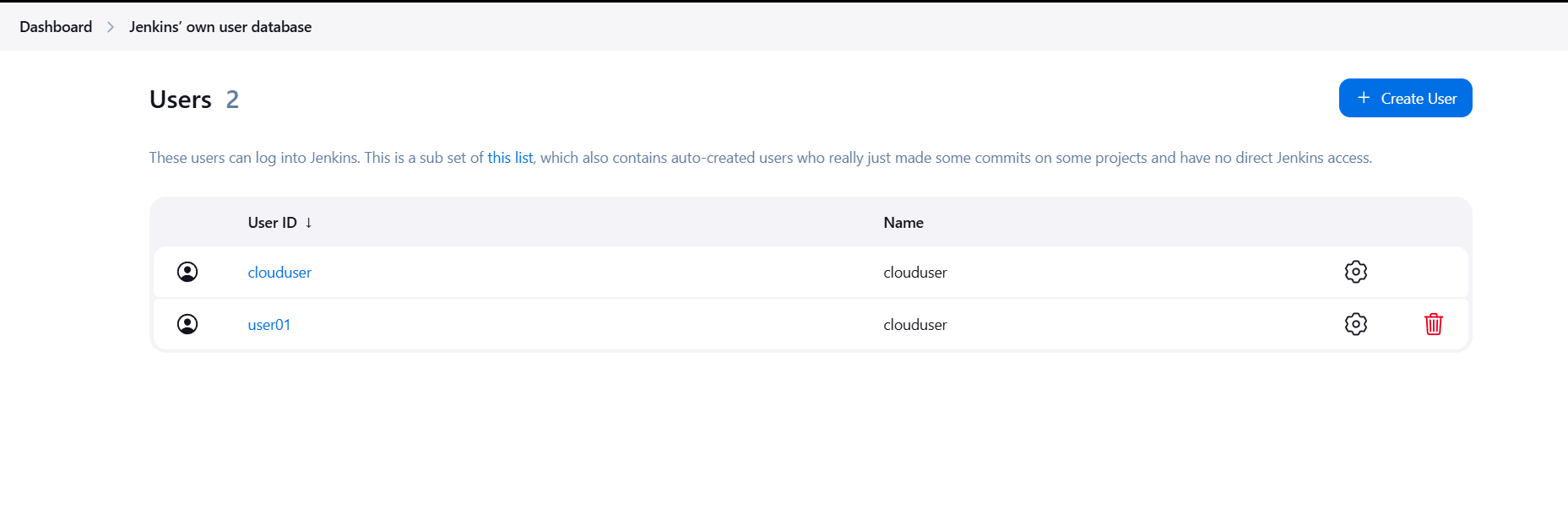
STEP 4: Configure Security for the new user.
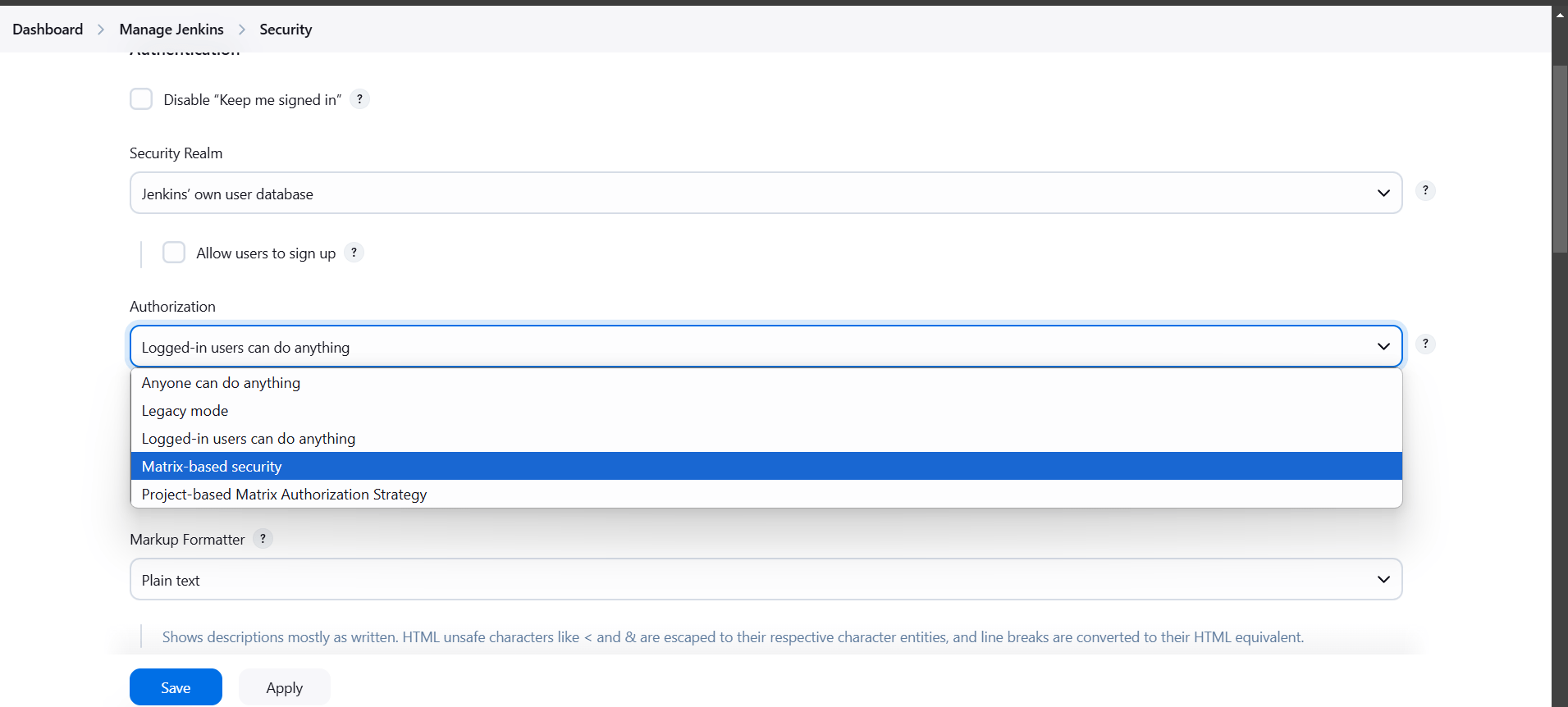
- Go to Jenkins dashboard and Click on manage Jenkins.
- Click on security.
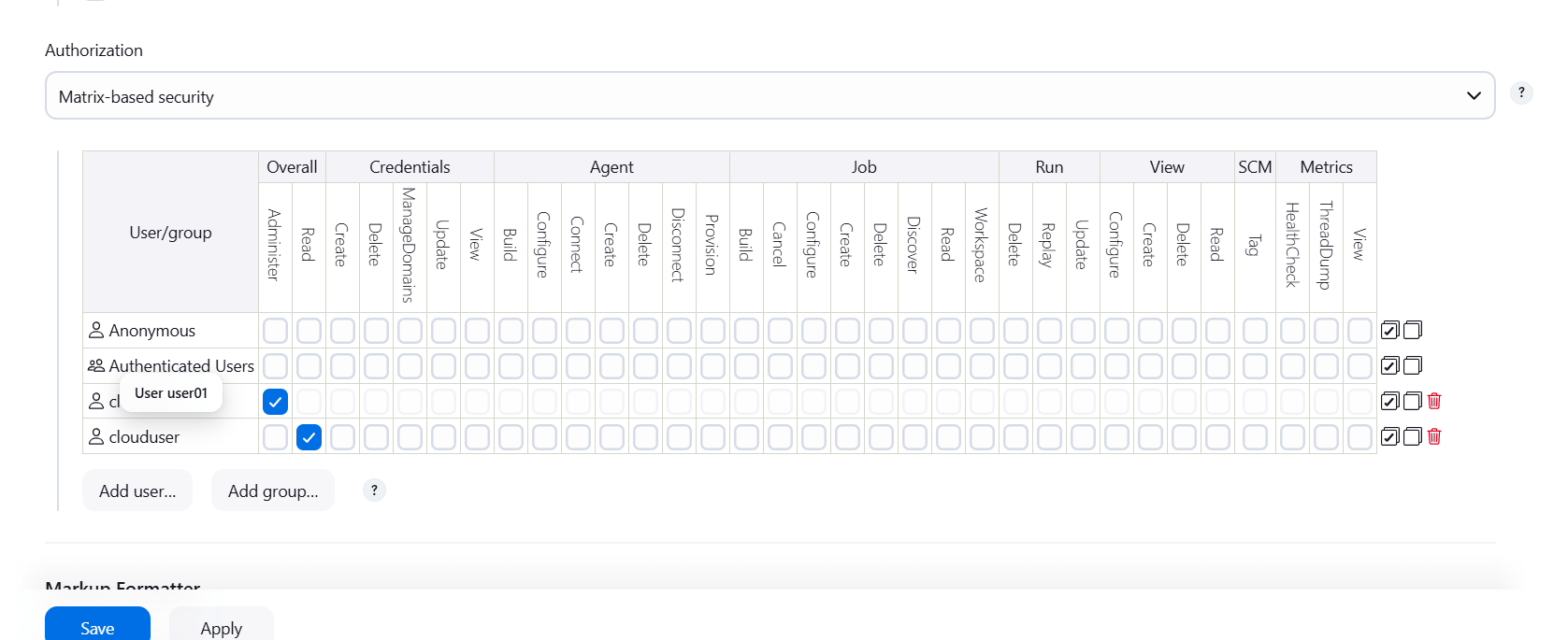
- Authorization: Matrix-based security.
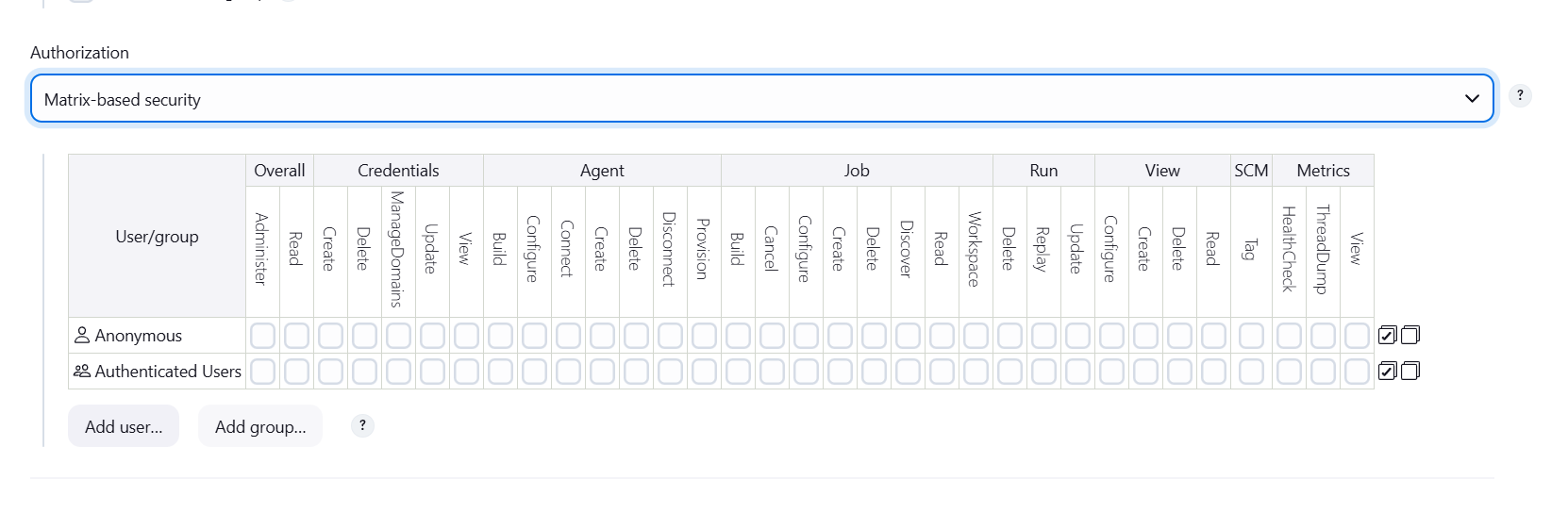
STEP 5: Click on add user.
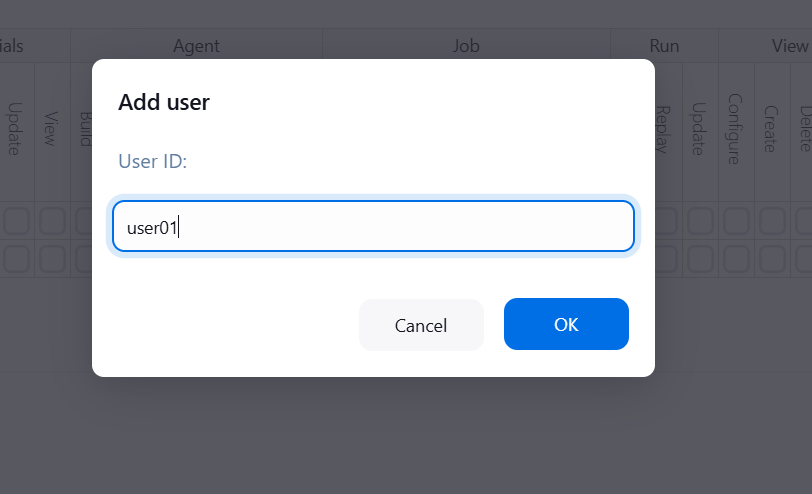
STEP 6: Enter user ID.
STEP 7: Add your created user.

STEP 8: Logout your Jenkins dashboard.
- Log in your created user.
STEP 9: Now go back to the initial account and give the permission to the user01.
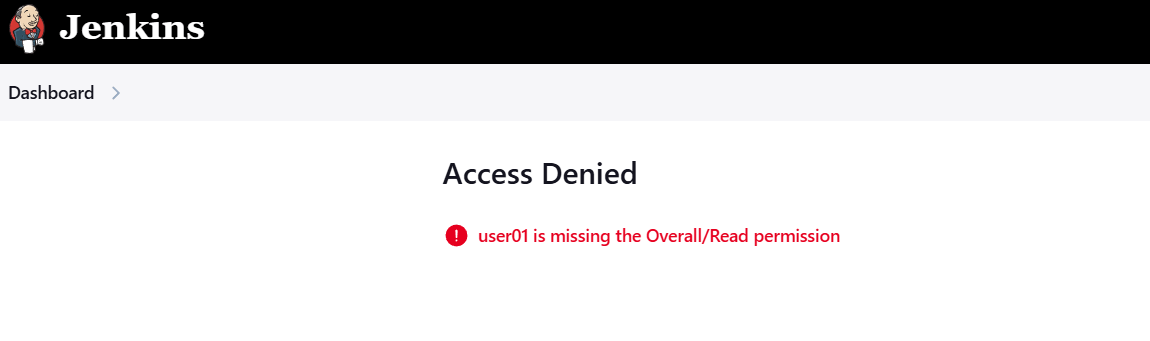
STEP 10: Click on read to your created user.
- Apply and save.
STEP 11: Now login to your created user.
Create Project–based Matrix Authorization Strategy
STEP 1:Go to manage Jenkins and Click on security.
- Select matrix based security.
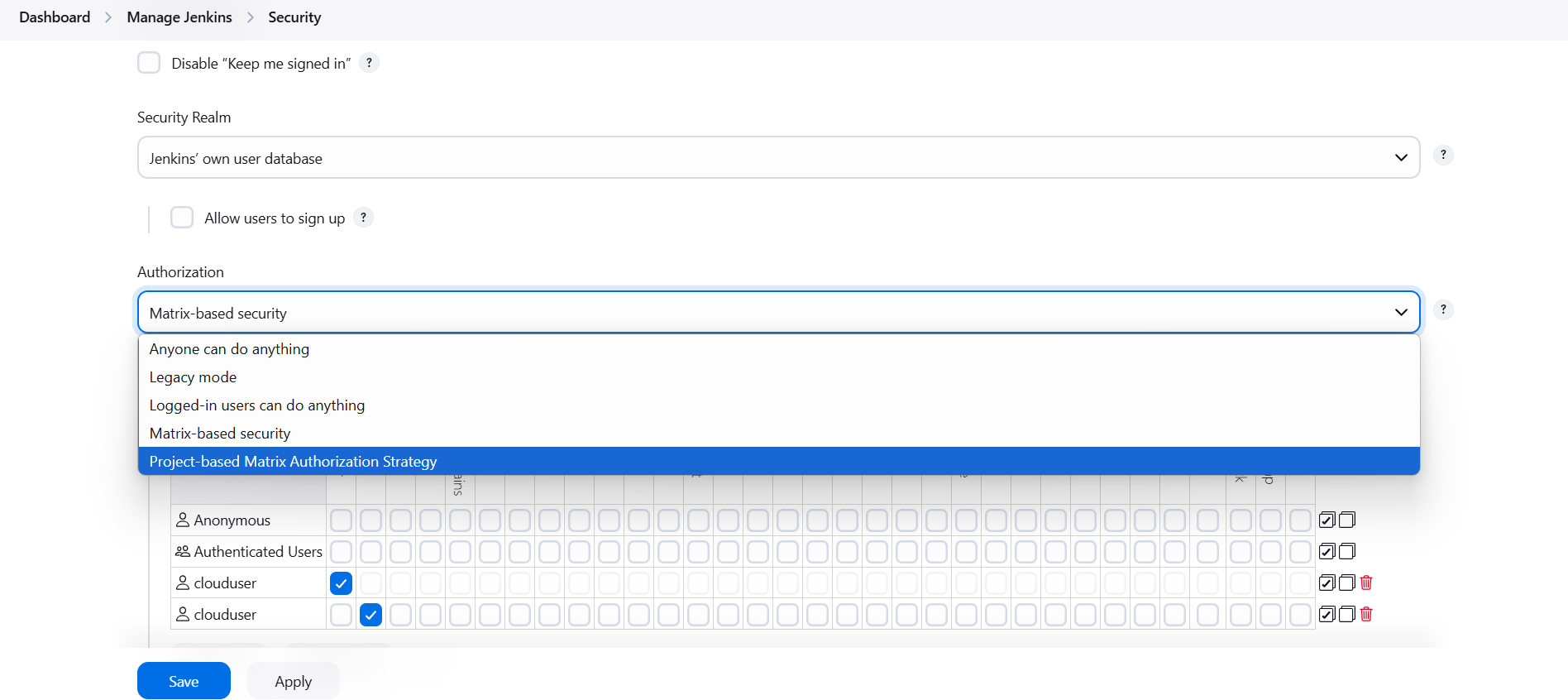
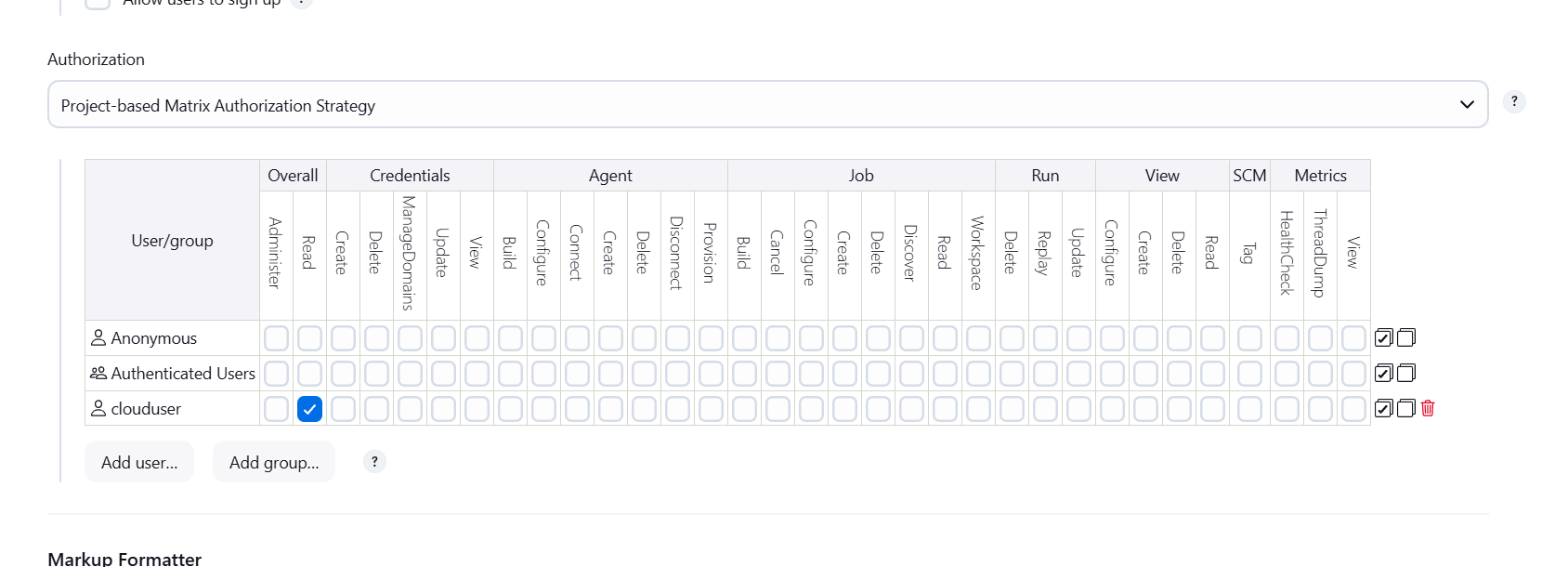
STEP 2: Click on read option.
- Apply and save.
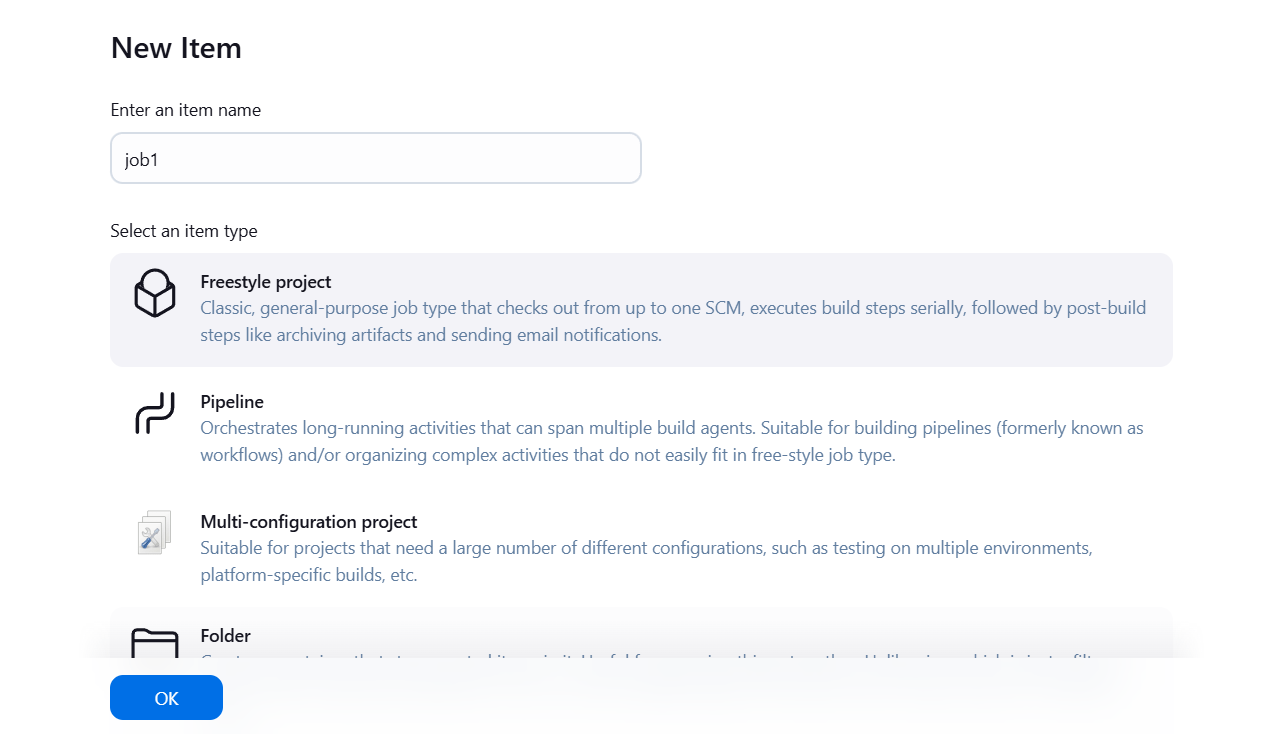
STEP 3: Create a new job.
- Select t freestyle project.
- Click on ok button.
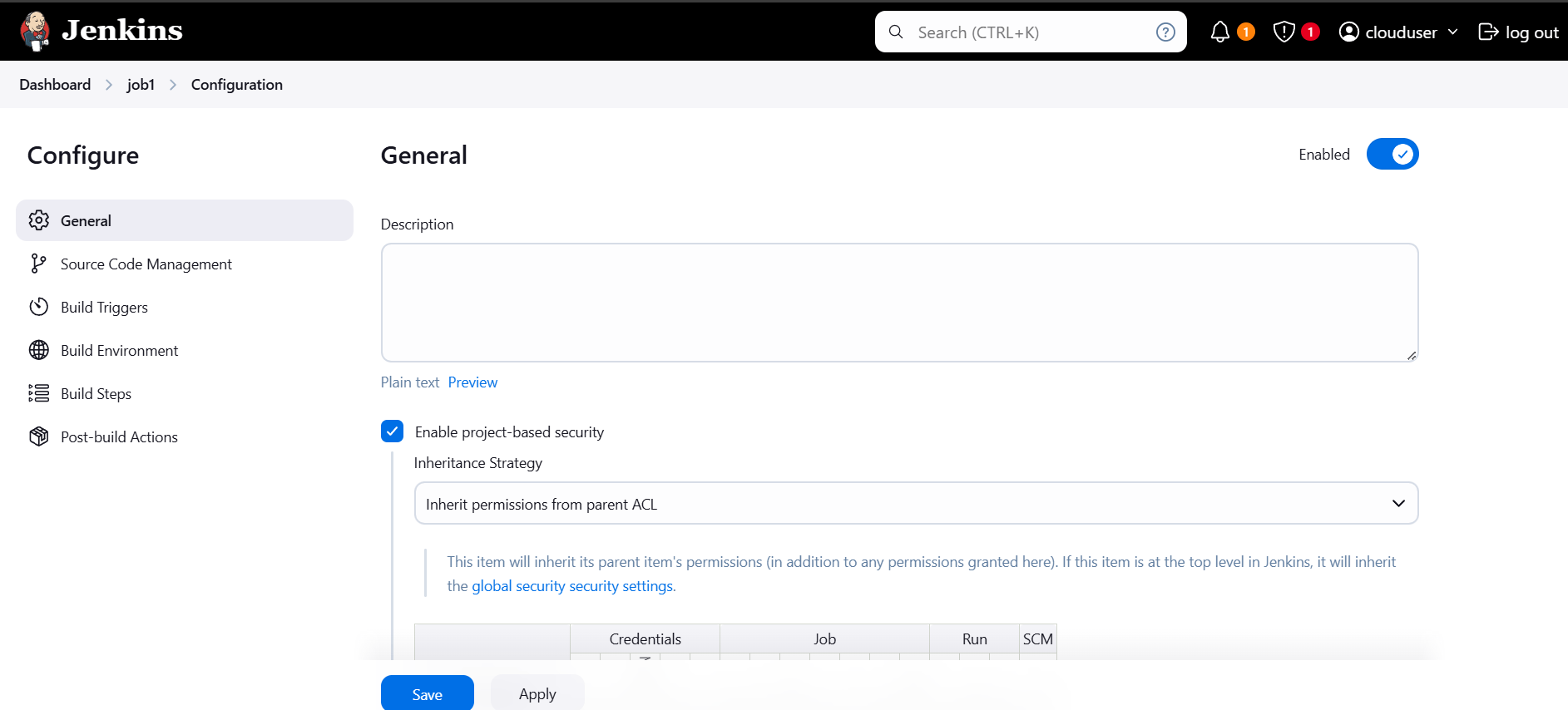
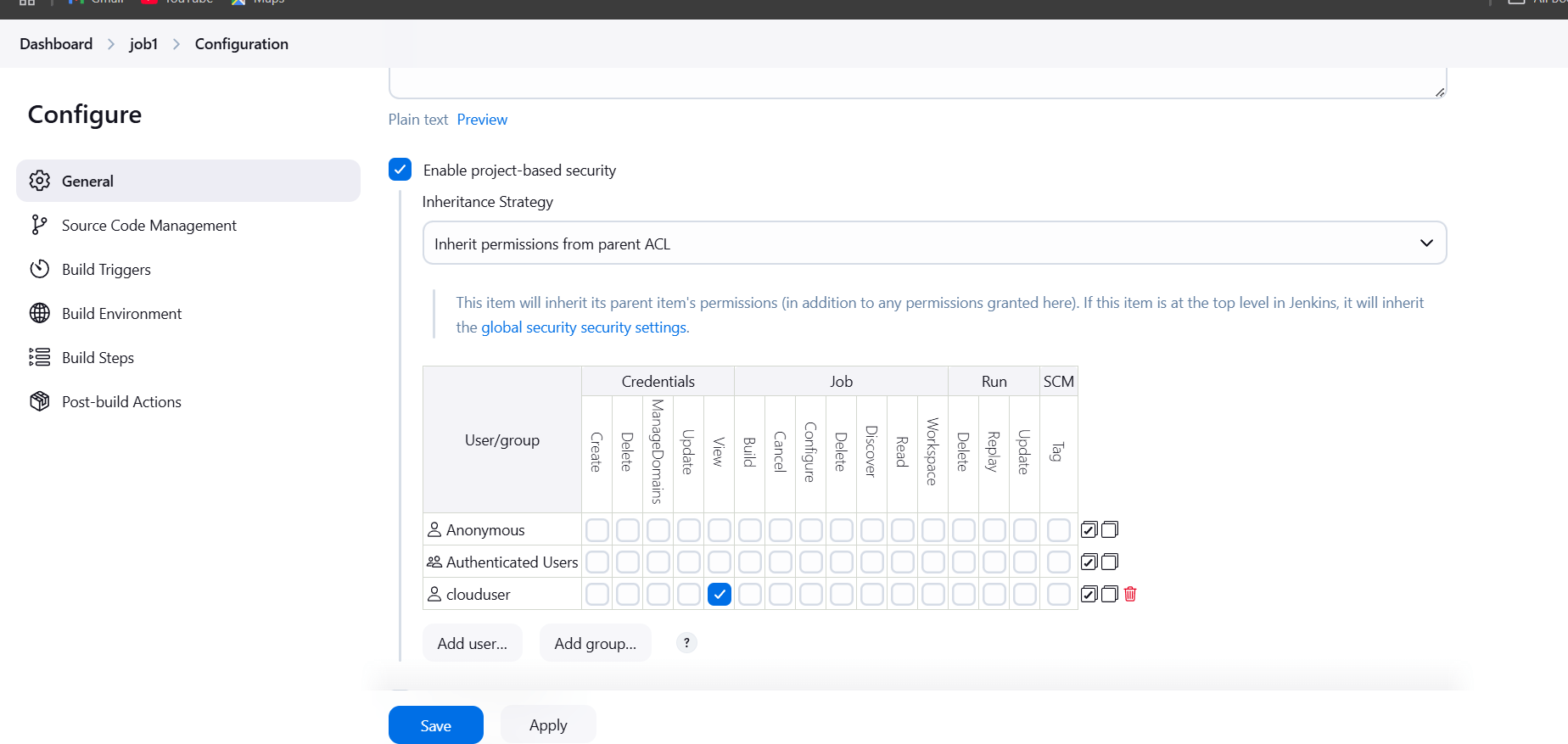
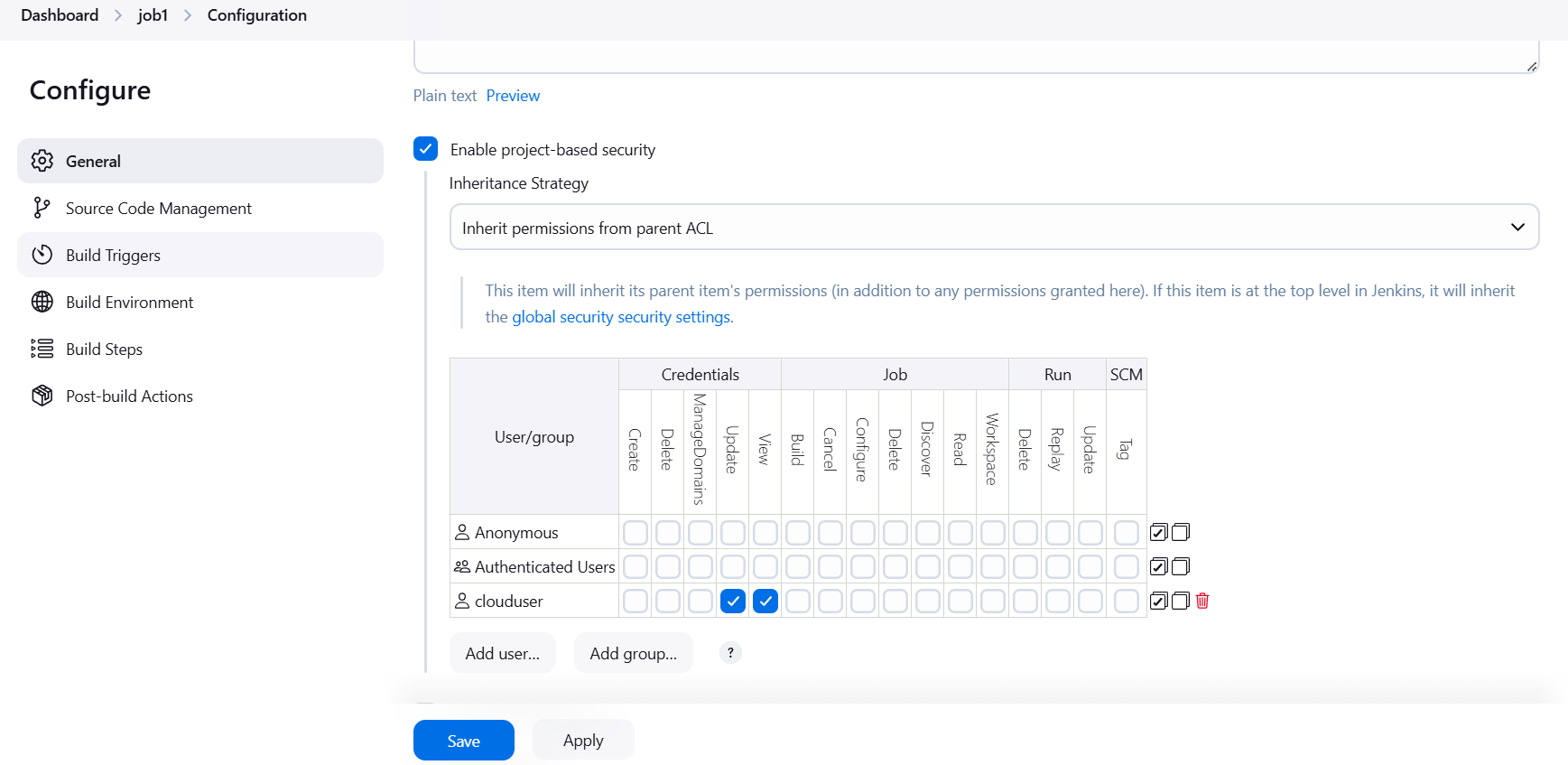
STEP 4: Enable project-based security.
- Select your created user.
- Tick on view and update option.
- Click on apply and save.
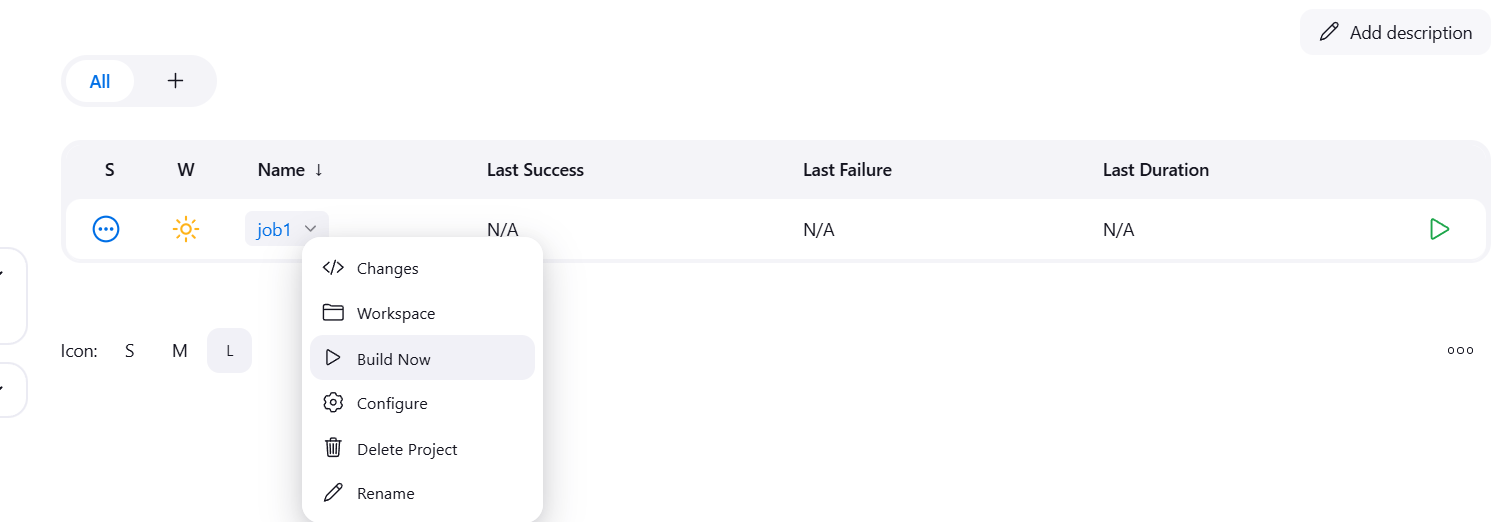
STEP 5: Click on build now.

Conclusion.
You have successfully configured the Matrix-Based Authorization Strategy, granting specific permissions to different users and groups, thereby ensuring controlled access to Jenkins resources.
You have successfully implemented the Project-Based Matrix Authorization Strategy, enabling project-specific permissions for users and groups, ensuring secure and tailored access to Jenkins jobs and pipelines.
By configuring these security practices correctly, Jenkins can be used safely to automate CI/CD processes without exposing sensitive information or opening the system to unauthorized access.

Add a Comment