Introduction.
In today’s rapidly evolving cloud landscape, ensuring endpoint security has become more critical than ever. As organizations increasingly migrate their workloads to the cloud, the need for robust protection against threats, malware, and unauthorized access grows in parallel. One of the most effective ways to bolster your cloud security posture is by leveraging AWS Endpoint Detection and Response (EDR). AWS EDR is designed to offer real-time threat detection, continuous monitoring, and automated responses to suspicious activities occurring across your cloud endpoints.
This guide aims to help you understand how to create, configure, and initialize AWS EDR from the ground up, even if you’re new to cloud security tools. We’ll walk through the core concepts, break down the essential steps, and provide practical tips to ensure your setup is both secure and scalable. By the end of this guide, you’ll not only understand how AWS EDR works but also how to effectively integrate it into your organization’s existing cloud environment.
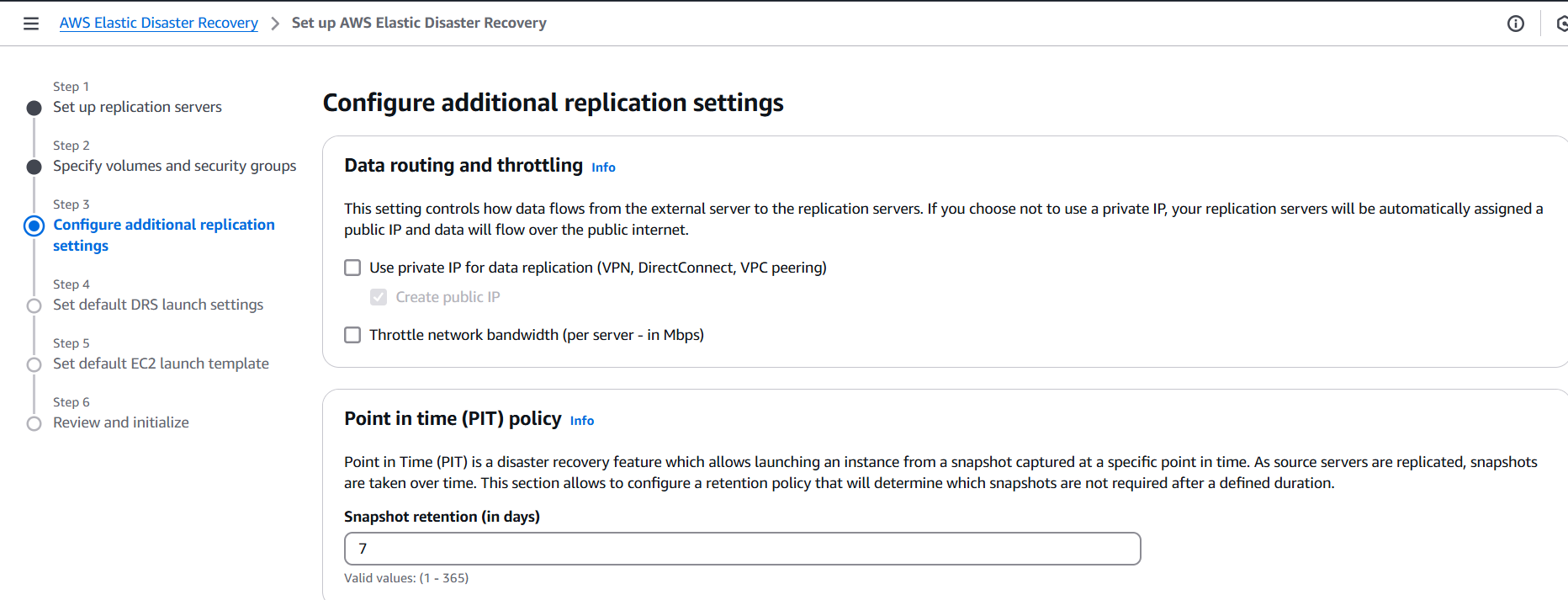
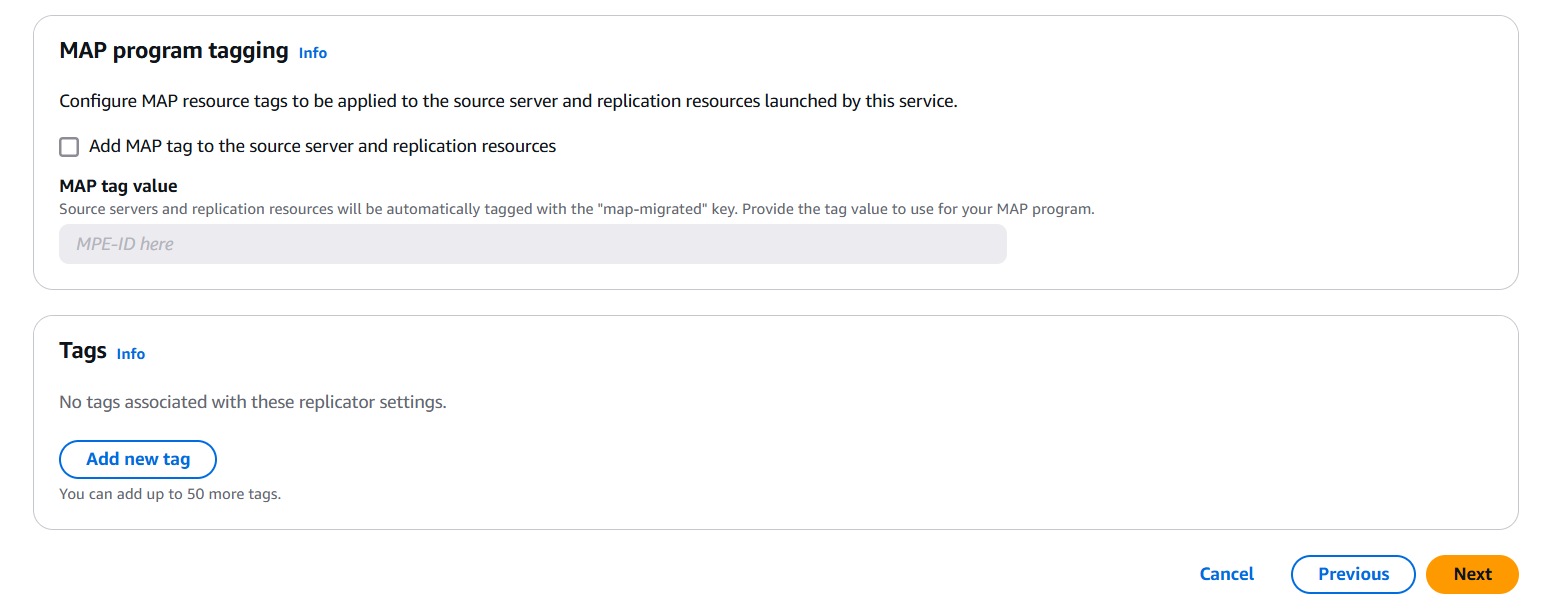
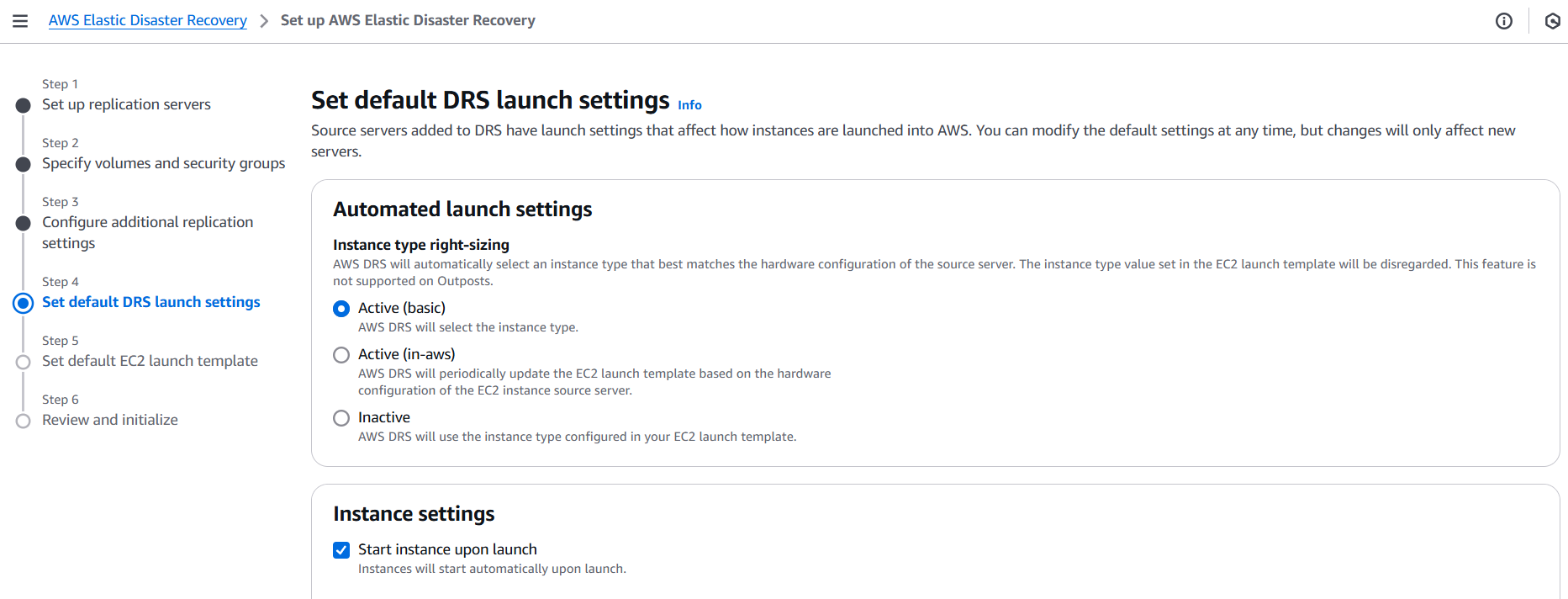
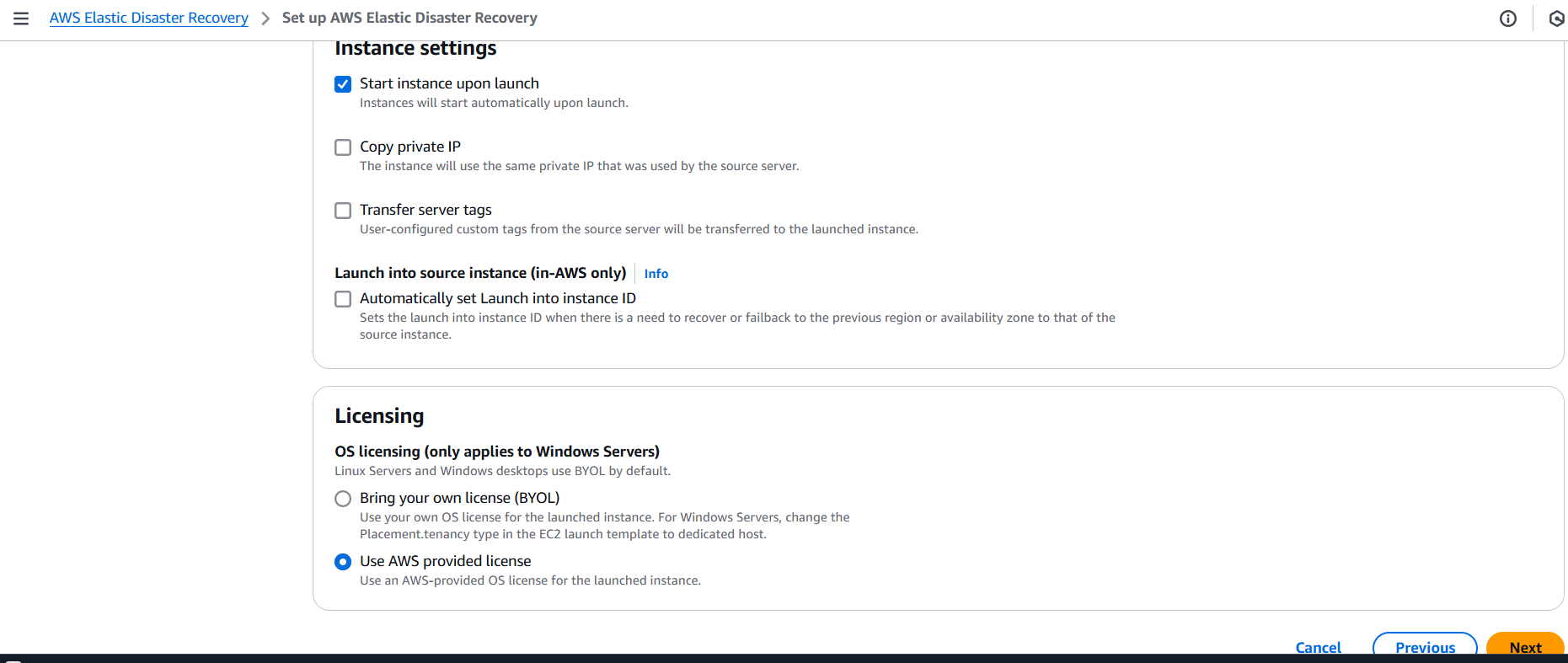
We’ll begin by explaining what AWS EDR is and why it plays a vital role in your AWS security stack. Next, we’ll explore its components—how it integrates with services like AWS Security Hub, Amazon GuardDuty, and AWS CloudTrail. Then, we’ll dive into the step-by-step process of setting it up: from enabling necessary services, setting up IAM roles and permissions, to configuring alerting and automated remediation.
Security professionals and DevOps teams alike can benefit from implementing AWS EDR to gain real-time visibility into potential threats and reduce response times significantly. Even for startups or small businesses using AWS, having a solid endpoint defense solution like EDR can mean the difference between a minor security hiccup and a major breach.
Whether you’re looking to protect EC2 instances, container workloads in ECS or EKS, or even hybrid environments, AWS EDR can be tailored to meet those needs. In this blog, we aim to make the setup process as simple and actionable as possible, with clear instructions and helpful insights along the way. You’ll also learn some best practices for maintaining and scaling your EDR configuration as your infrastructure grows.

Cybersecurity doesn’t have to be overwhelming or overly complex, especially with tools like AWS EDR that are built to integrate seamlessly into your AWS workflow. So, if you’re ready to enhance your cloud security and gain greater control over your endpoints, let’s dive in and get started with AWS EDR from scratch.
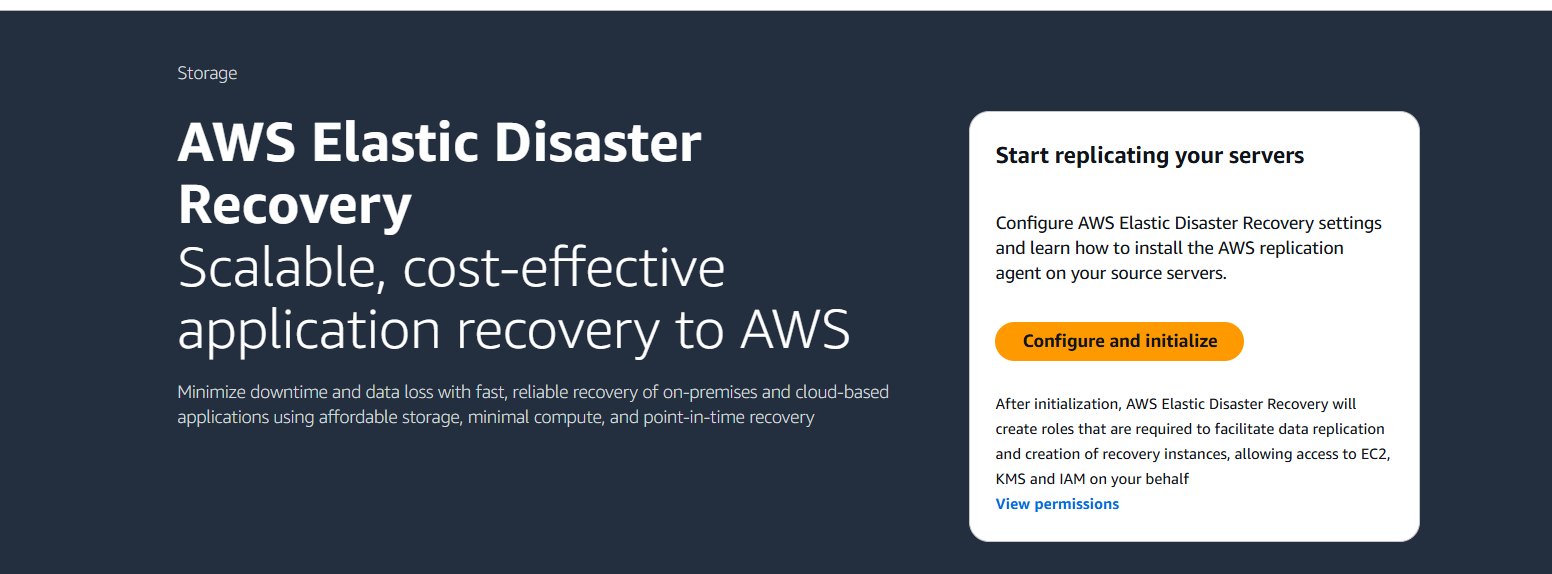
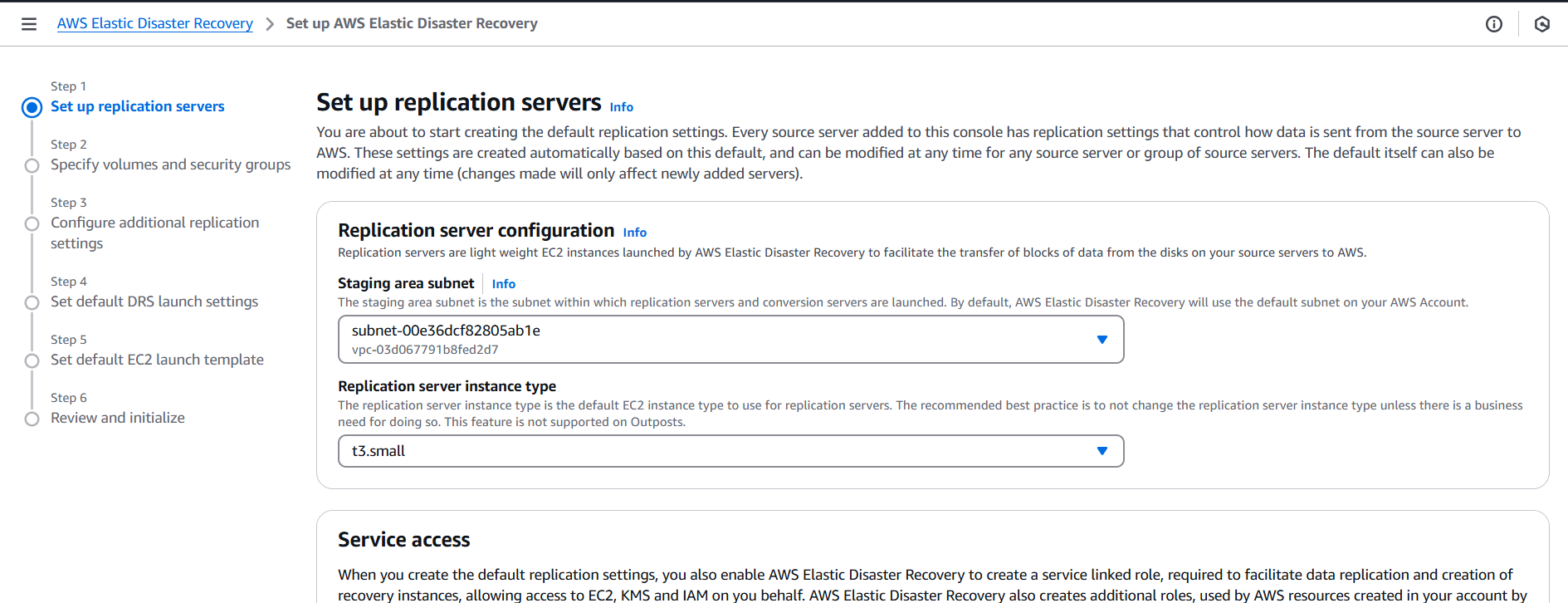
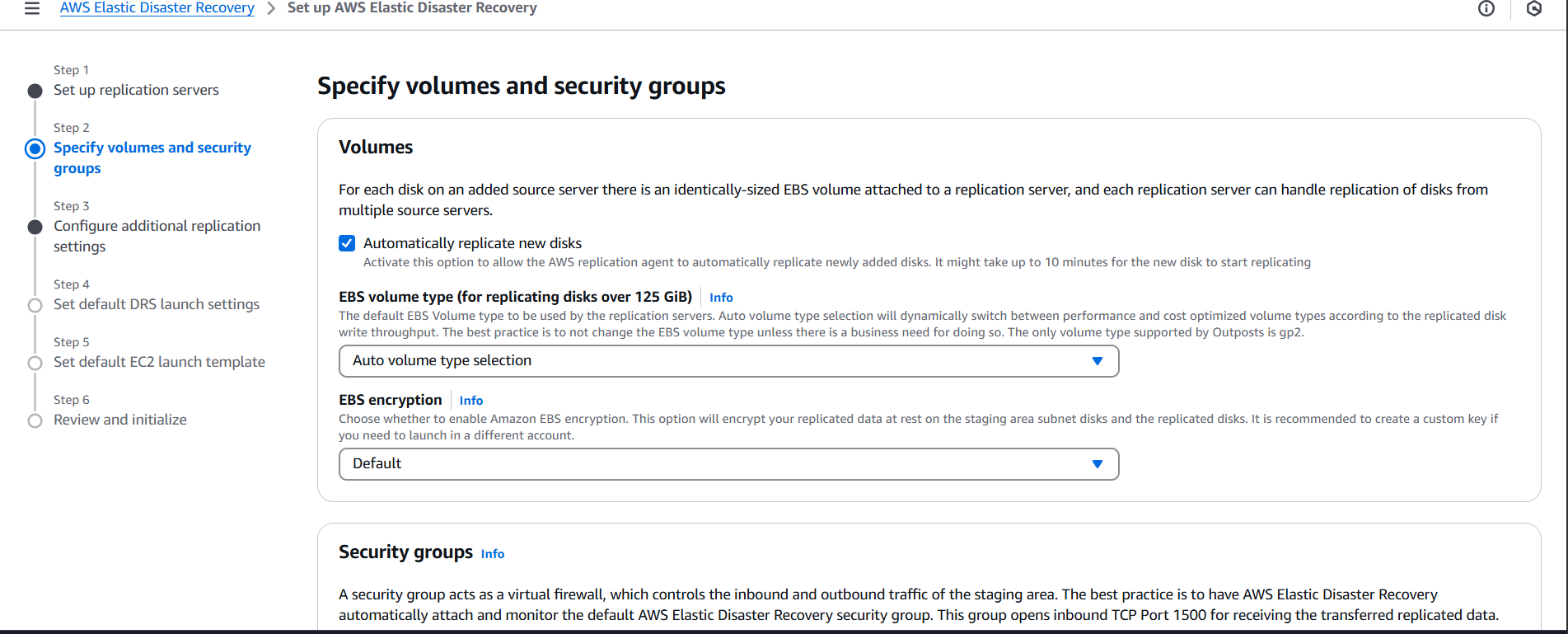
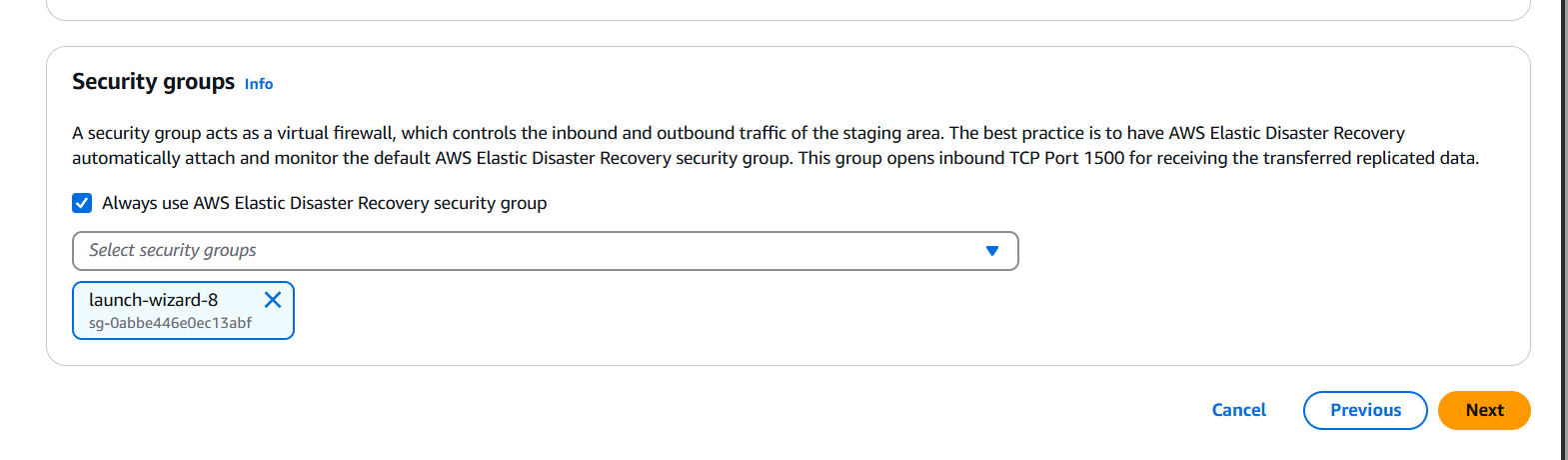
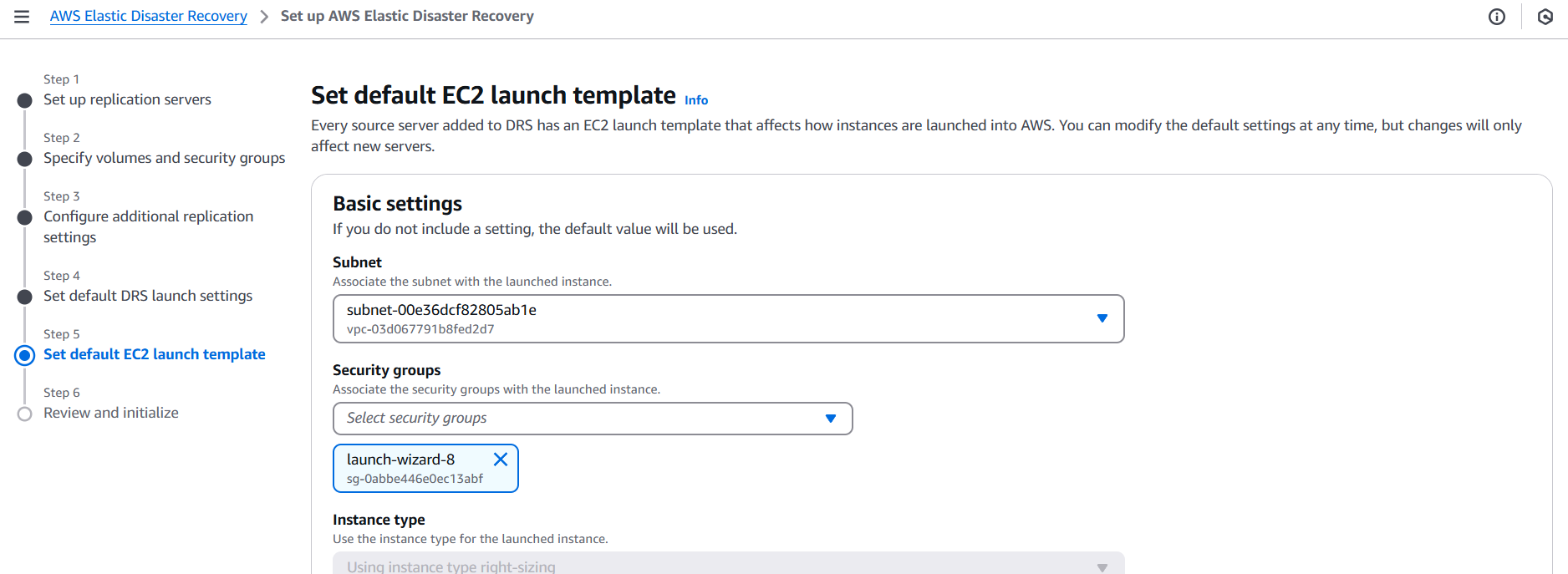
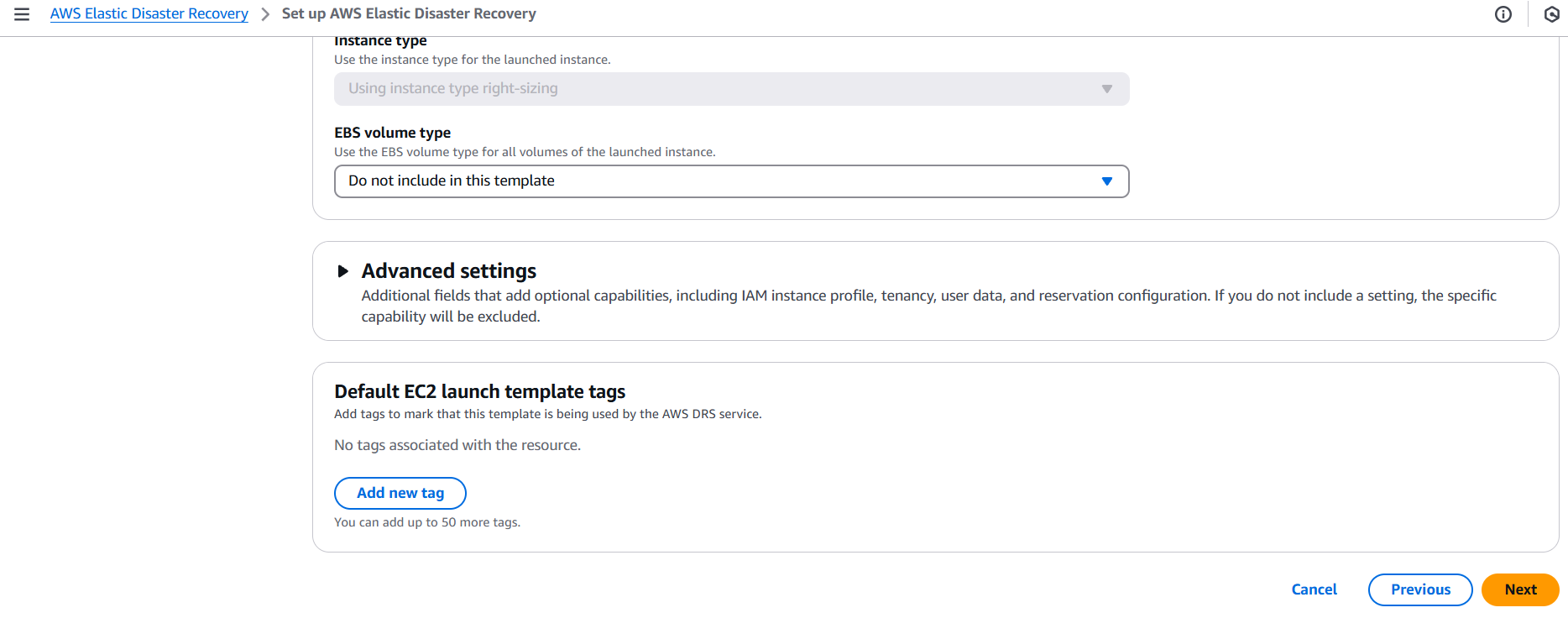
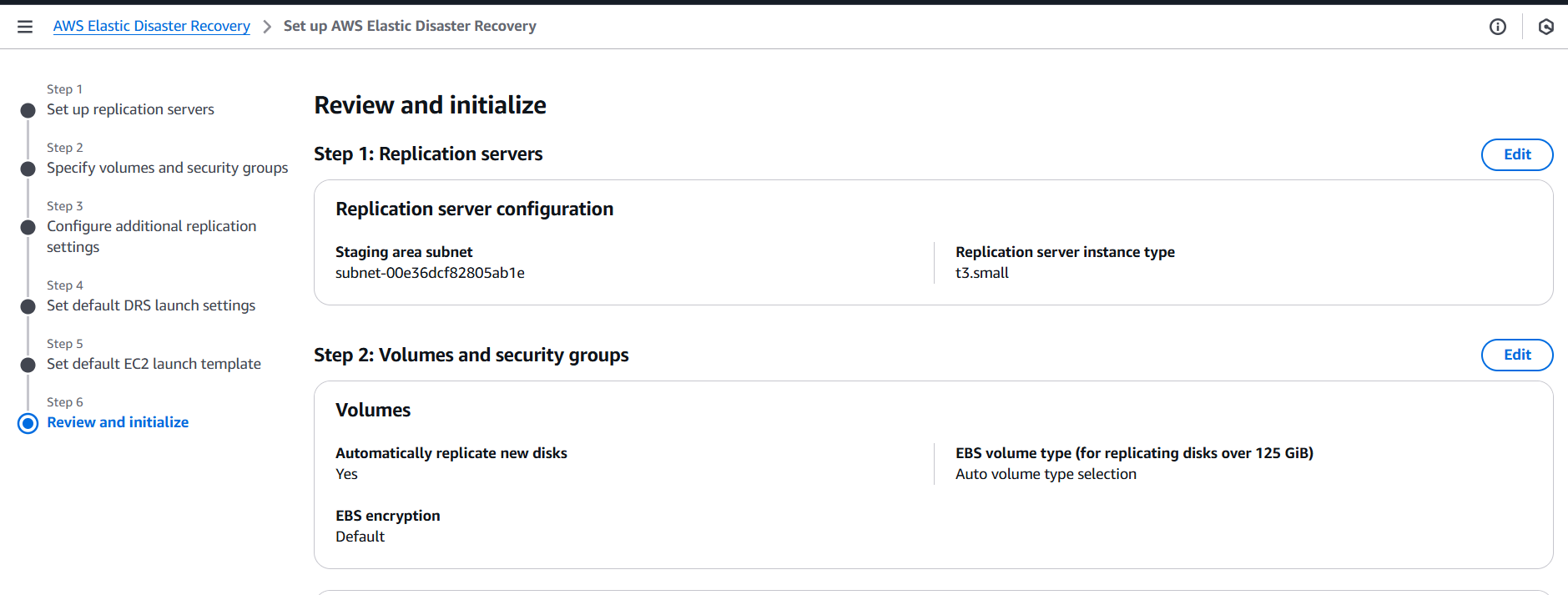
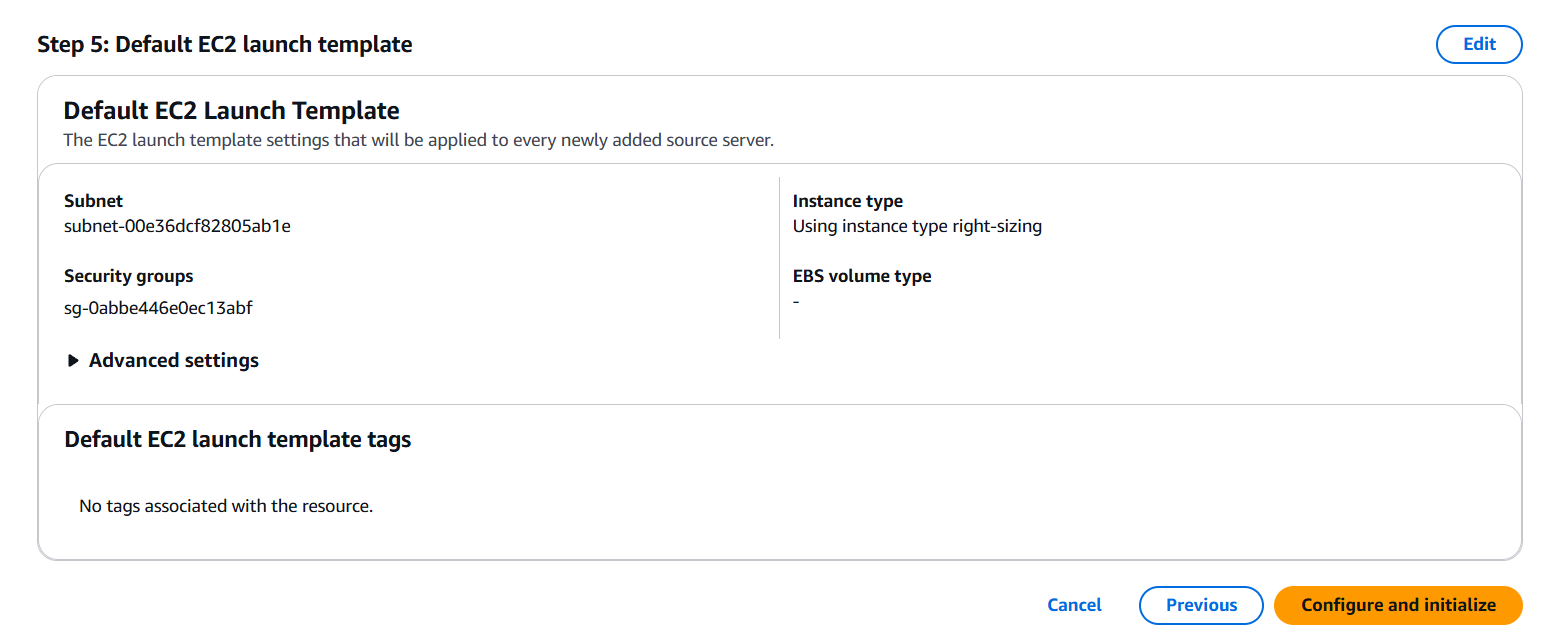

Conclusion.
Securing your cloud environment is no longer optional—it’s a necessity. In this blog, we’ve walked through the essential steps to create, configure, and initialize AWS Endpoint Detection and Response (EDR), providing a solid foundation for endpoint protection within your AWS infrastructure. From enabling key services like GuardDuty and CloudTrail, to setting up IAM permissions and fine-tuning alert configurations, each step plays a critical role in building a responsive and resilient security posture.
By leveraging AWS EDR, you gain more than just visibility—you gain the ability to act swiftly when threats are detected. Automated detection, real-time monitoring, and intelligent alerting are all designed to minimize risks and reduce response times, giving your team the edge it needs in an increasingly hostile digital landscape.
As your cloud architecture grows, so should your security strategy. Fortunately, AWS EDR is designed to scale with your infrastructure, offering flexible integration with AWS-native services and third-party tools. Remember, setting up EDR is not a one-time task—it’s the first phase of a broader, ongoing effort to ensure endpoint security across your entire environment.
Whether you’re part of a small startup or a large enterprise, understanding how to implement EDR properly is a crucial step toward proactive cloud defense. With the right configuration and regular monitoring, you can rest easier knowing your endpoints are being actively protected.
Now that you’ve got the basics covered, you’re well on your way to building a safer, more secure AWS environment. Keep iterating, stay updated on AWS security best practices, and continue refining your EDR setup as new threats emerge. Security is a journey—and with AWS EDR, you’ve taken a major step in the right direction.

Add a Comment