Introduction.
In the modern cloud landscape, customer data security isn’t just a technical requirement—it’s a competitive differentiator. As organizations increasingly migrate to cloud-native platforms, they demand greater control over how their data is encrypted, who can access it, and how encryption keys are managed. Enter Customer-Managed Keys (CMKs) on AWS Key Management Service (KMS), a powerful feature that allows customers to own and operate their encryption keys, while service providers integrate these keys into their applications without ever directly managing them. This paradigm shift in data control helps meet compliance needs like GDPR, HIPAA, and PCI-DSS, while simultaneously building trust between providers and their users.
For software providers and SaaS companies, enabling customer-managed encryption is no longer a luxury—it’s a strategic necessity. When you allow your customers to bring and control their own KMS keys, you’re not just enhancing security; you’re empowering them with autonomy, transparency, and peace of mind. This model is especially critical in industries like finance, healthcare, and government, where data sovereignty and strict auditing are non-negotiable. By offering customer-managed services built on KMS, you signal a strong commitment to data ownership and compliance readiness.
So, what does it take to build a customer-managed service using AWS KMS? At its core, it involves separating encryption responsibilities: you manage the infrastructure and application logic, while the customer manages the encryption keys via their own AWS account. This means you need to architect your services to request permissioned access to customer-owned CMKs, handle encryption/decryption securely, and gracefully manage key revocation, rotation, and access changes. Done right, it creates a seamless experience where your system can operate securely without compromising customer control.
This blog walks you through the entire process—starting from understanding KMS fundamentals, defining roles and permissions, implementing secure key access via AWS SDKs or CLI, handling lifecycle events, and providing clear documentation to your customers for onboarding. We’ll also explore best practices around key policy design, grant usage, audit logging, and fault-tolerant design patterns to ensure your service is not only secure but also resilient and compliant.
By the end of this guide, you’ll have a clear roadmap to design and deploy services that leverage customer-managed encryption in AWS, offering your users a security model where they truly hold the keys. Whether you’re building a SaaS product, a cloud-native platform, or managing sensitive data workflows, this approach will position your service as trustworthy, future-ready, and aligned with modern enterprise expectations. Let’s dive in.

Steps to Create a Customer Managed Service on AWS KMS
1. Use Customer-Provided KMS Keys (CMKs)
- Customers create and manage their own KMS keys.
- You integrate with those keys to encrypt/decrypt data.
Example AWS Services that support this:
- S3 with KMS
- EBS with KMS
- RDS with KMS
- Custom apps using AWS SDK to encrypt with KMS
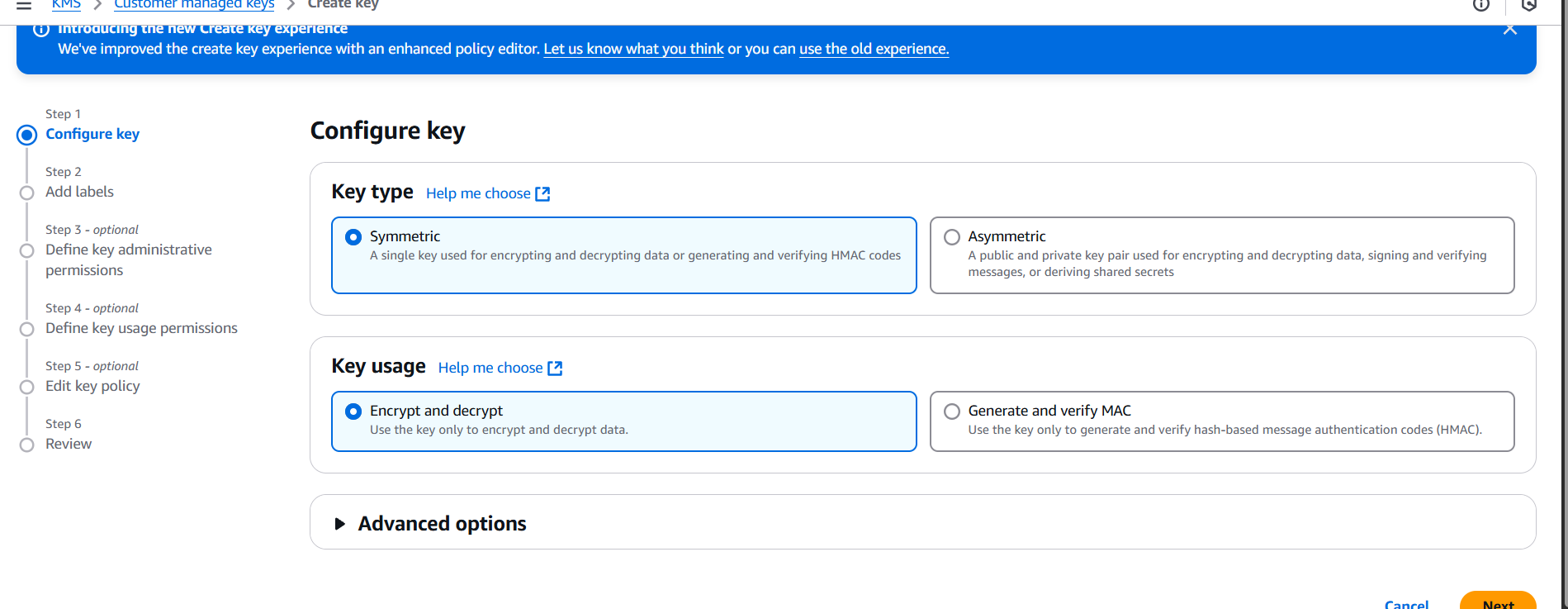
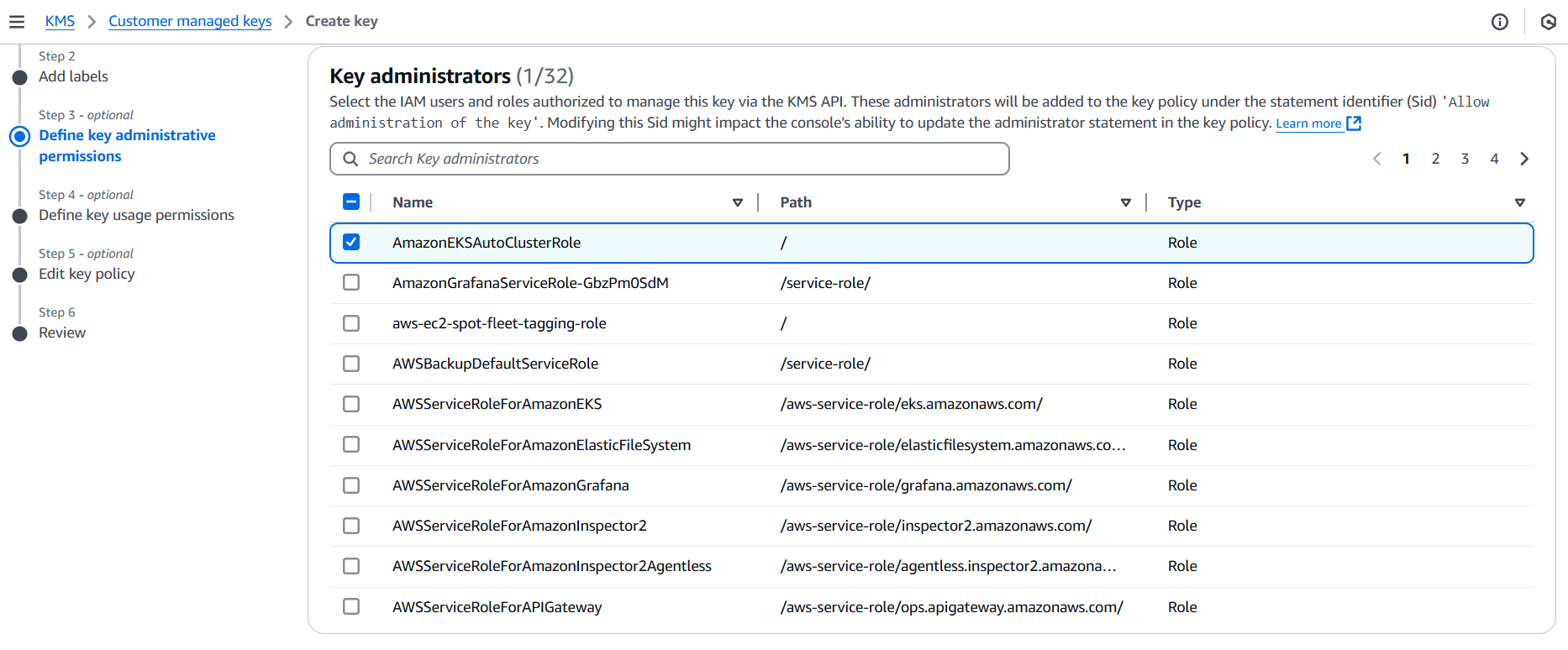
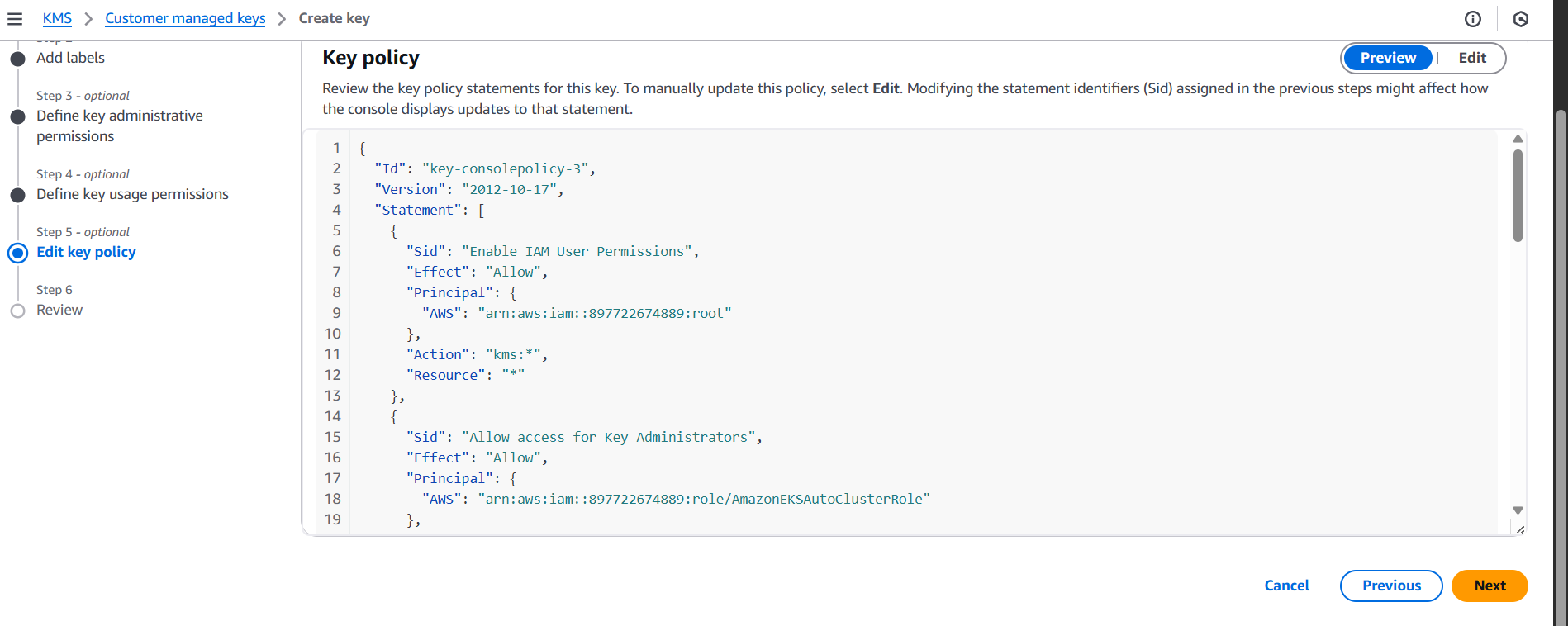
2. Define the Key Policy Model
Customers must grant your service permissions to use their CMK.
Your service account needs:
{
"Sid": "AllowServiceToUseKey",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<your-service-account-id>:role/<service-role>"
},
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:GenerateDataKey"
],
"Resource": "*"
}Customers apply this in the KMS key policy.
3. Encrypt Customer Data Using the CMK
- Use the
kms:Encryptorkms:GenerateDataKeyAPI from the customer’s CMK. - Example in Python:
import boto3
kms = boto3.client('kms')
response = kms.encrypt(
KeyId='arn:aws:kms:us-east-1:customer-account-id:key/key-id',
Plaintext=b'Some secret data'
)
ciphertext = response['CiphertextBlob']4. Design for Least Privilege
- You must only access the CMK when needed.
- Ensure your service cannot modify or delete the CMK.
5. Audit and Logging
- Recommend customers enable:
- CloudTrail logs for KMS usage
- Key rotation
- KMS grants (temporary access)
6. Handle Key Revocation
- Your service should gracefully handle scenarios where:
- The key is disabled or deleted
- Your access is revoked
- Key rotation happens
Add fallback logic or alerts to prevent data loss.
7. Document Integration Steps for Customers
Provide a simple onboarding guide:
- How to create a KMS CMK
- How to set up IAM policies and key policy
- How to give your service access


Conclusion.
Building customer-managed services using AWS KMS isn’t just a technical enhancement—it’s a strategic step toward deeper customer trust, improved compliance alignment, and long-term service differentiation. By allowing your customers to manage their own encryption keys, you offer them the ability to own their security posture without compromising the functionality or performance of your platform. It’s a win-win approach: you handle the infrastructure, scalability, and availability, while your customers retain control over how, when, and where their data is protected.
Throughout this guide, we’ve explored the foundational concepts of AWS Key Management Service, the distinction between provider-managed and customer-managed encryption models, and the critical components required to support CMKs in a multi-tenant service architecture. You’ve seen how to request access to customer-owned keys securely, enforce least-privilege access using IAM roles and policies, and implement best practices like auditing, logging, and graceful failure handling. These are more than just technical patterns—they form the backbone of a modern, compliance-ready service.
One of the most important takeaways is that enabling customer-managed keys doesn’t mean giving up control—it means shifting it to the right hands. It requires careful design, thoughtful documentation, and proactive support, but the rewards are clear: increased adoption from security-conscious enterprises, smoother onboarding in regulated industries, and a reputation for putting customer needs first. This model sends a clear message: your platform is built with transparency and flexibility at its core.
As more organizations demand accountability in the way their data is handled, customer-managed encryption will become a baseline expectation rather than a premium feature. By embracing this architecture early, you position your business as a forward-thinking provider that is aligned with the evolving cloud security landscape. In doing so, you reduce the friction around procurement and security reviews, opening doors to larger deals and longer-term partnerships.
Looking ahead, consider how this approach can be extended—whether through automation of key grant creation, enhanced key lifecycle tooling, or integration with multi-cloud key management strategies. And don’t forget to keep educating your customers: the easier you make it for them to bring their own keys and trust your service, the more likely they are to stay.
Ultimately, customer-managed services on AWS KMS are about empowering your users without overburdening your operations. With the right mindset, tooling, and architecture, you can build services that not only meet today’s demands but are ready for tomorrow’s expectations. So start small, iterate securely, and give your customers the confidence to take ownership of their data—because in the cloud, trust is everything.

Add a Comment