Introduction.
In today’s cloud-driven world, security is everything — and nowhere is that more evident than in the way access is managed within Amazon Web Services (AWS). Whether you’re a beginner stepping into cloud infrastructure or a seasoned developer looking to sharpen your cloud security skills, understanding IAM (Identity and Access Management) policies is essential. IAM is AWS’s core service for managing who has access to what within your AWS account. It determines what resources users can access and what actions they can perform — making it a foundational piece of your cloud architecture.
So, what exactly is an IAM policy? Simply put, it’s a document written in JSON (JavaScript Object Notation) that defines permissions. These policies specify the actions (like reading an S3 bucket or starting an EC2 instance), the resources those actions apply to, and any optional conditions that further control access. Policies can be attached to IAM users, groups, or roles, allowing you to enforce granular, role-based access control across your AWS environment.
The power of IAM policies lies in their flexibility and precision, but that same power can also make them seem complex and intimidating to beginners. One small misconfiguration can unintentionally lock users out of critical resources or open up potential security vulnerabilities. That’s why it’s crucial to learn not just how to write policies, but also how to understand and validate them.
In this guide, we’ll walk through the entire process of creating IAM policies, starting from the basic structure to real-world examples and best practices. We’ll explain the key components of a policy document — such as the “Version,” “Statement,” “Effect,” “Action,” “Resource,” and “Condition” elements — and how they come together to define what is and isn’t allowed. You’ll learn how to use the AWS Management Console to build policies visually, as well as how to write and apply custom policies using JSON and the AWS CLI.
We’ll also cover important concepts like least privilege, service-specific permissions, and policy evaluation logic — all of which play a role in designing secure and effective access control. In addition, we’ll look at common use cases, such as granting read-only access to S3, full access to Lambda functions, or restricting actions to specific IP addresses. Each example will come with a breakdown so you can fully understand what the policy is doing and how to tweak it for your own needs.
Whether you’re managing a small app on AWS or part of a team running enterprise-scale cloud workloads, creating the right IAM policies ensures that your infrastructure stays secure, compliant, and efficient. AWS offers plenty of built-in policies, but learning how to craft your own gives you the flexibility to support unique requirements and fine-tune permissions at every level.
By the end of this post, you’ll be able to confidently create IAM policies tailored to your organization’s needs — and more importantly, understand why they work. Ready to become an IAM policy pro? Let’s dive in.

Steps to Create an IAM Policy
Option 1: Using the AWS Management Console
- Log in to your AWS Management Console.
- Go to IAM.
- In the sidebar, click Policies.
- Click Create policy.
- Choose:
- Visual editor (for building policies step-by-step)
- JSON (to paste/write your own policy)
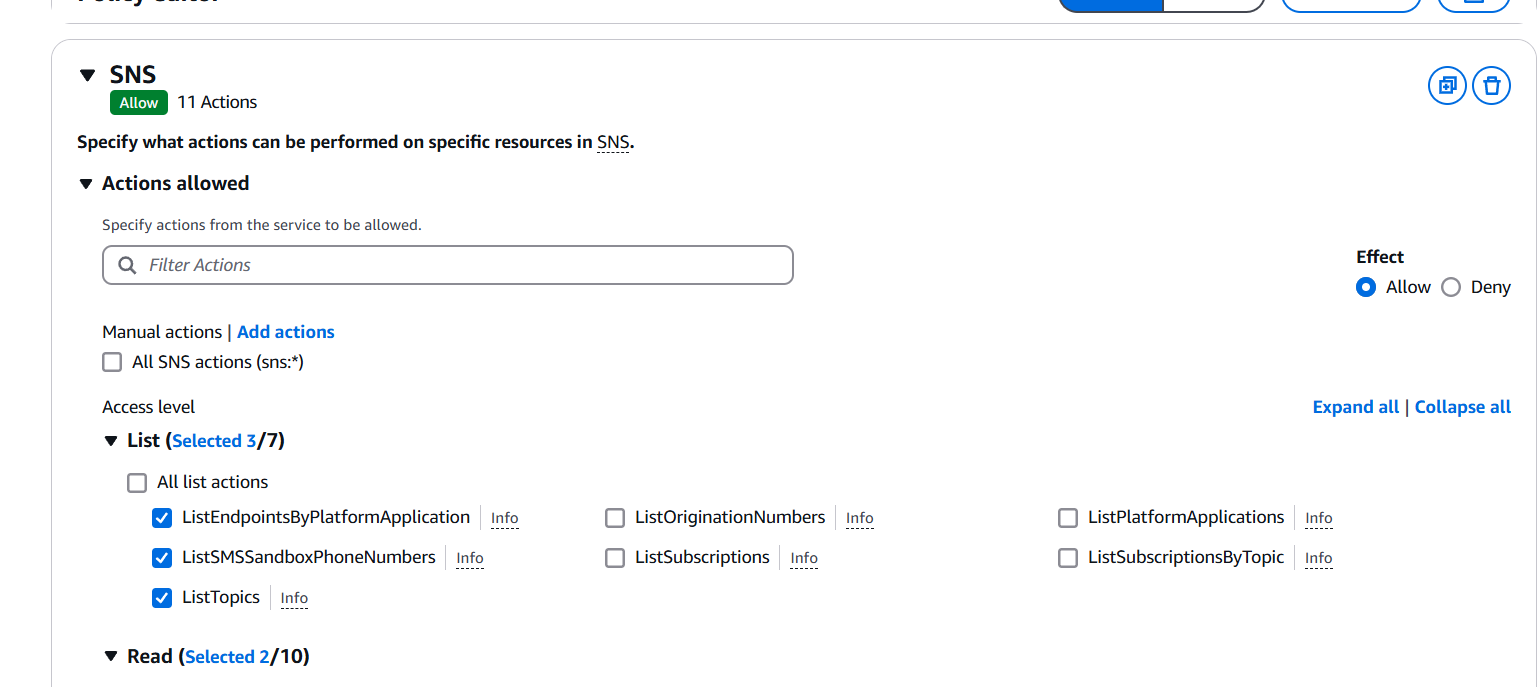
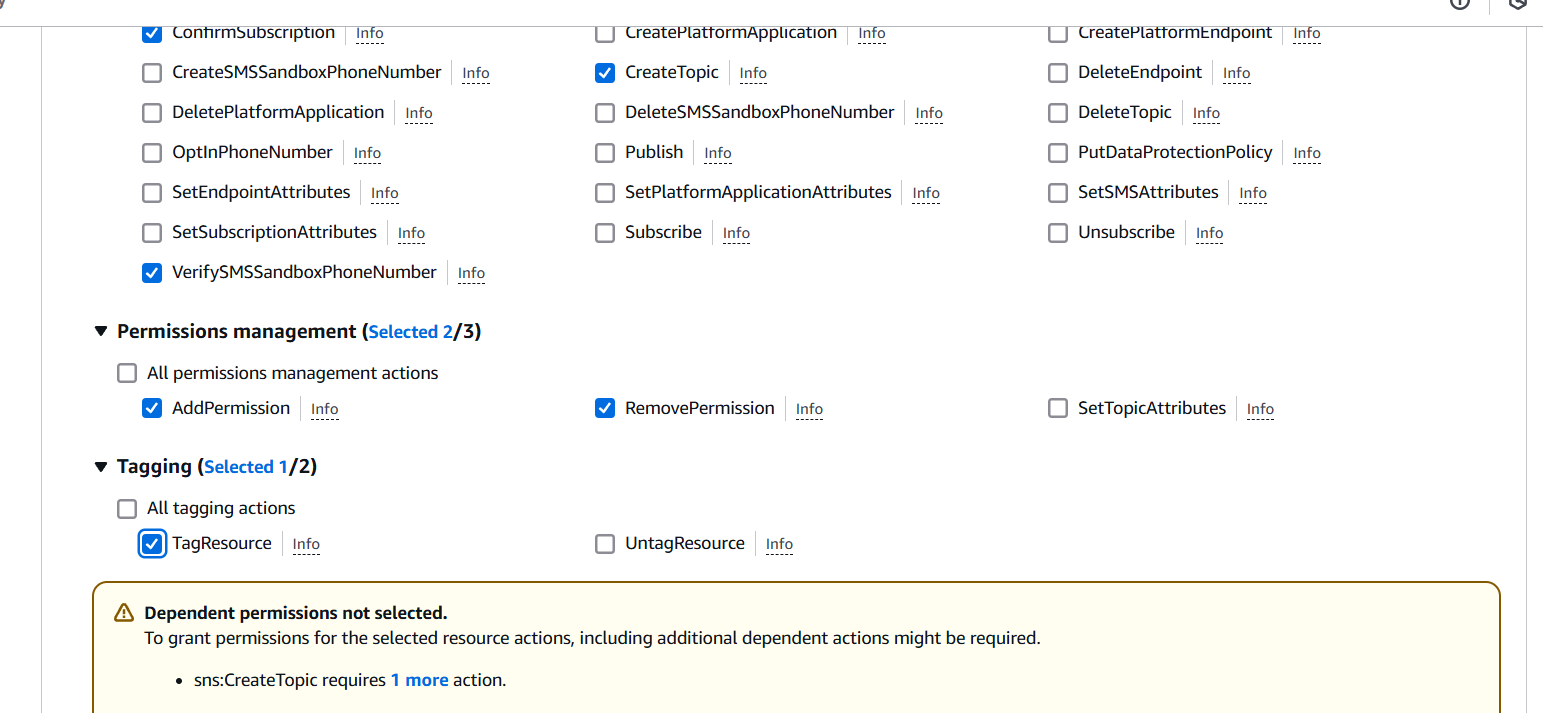
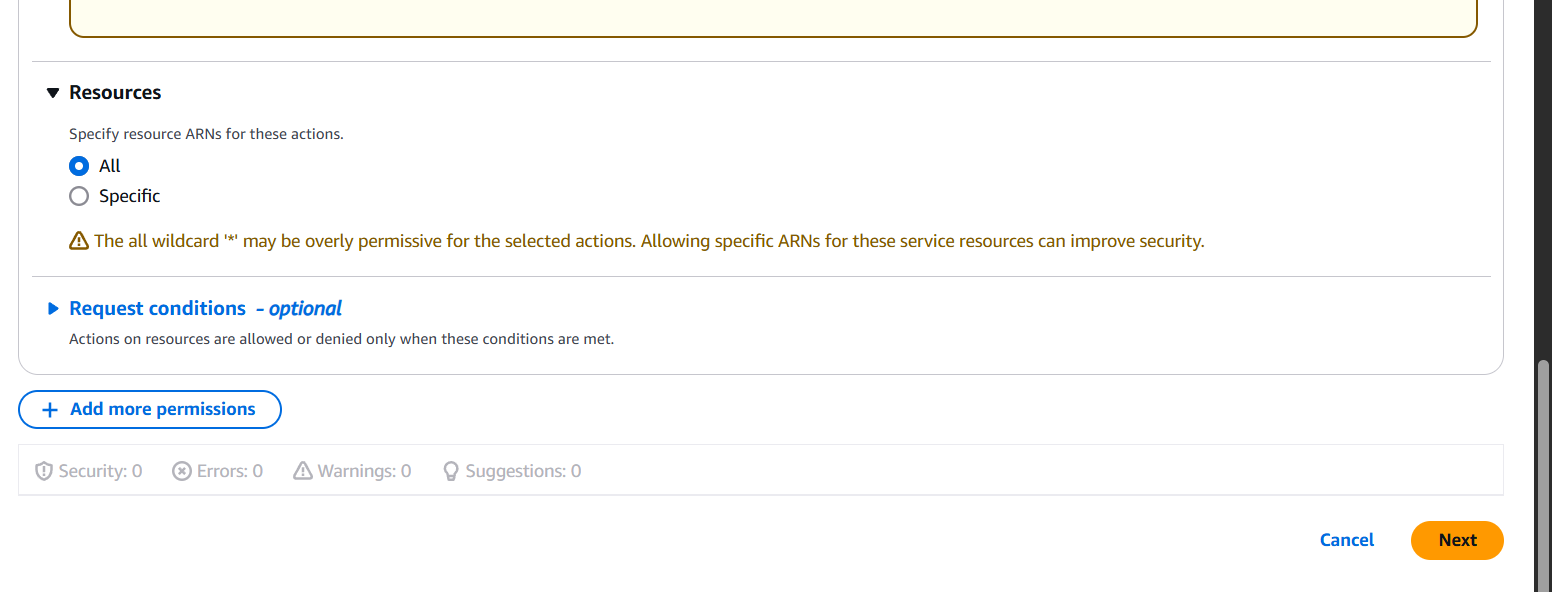
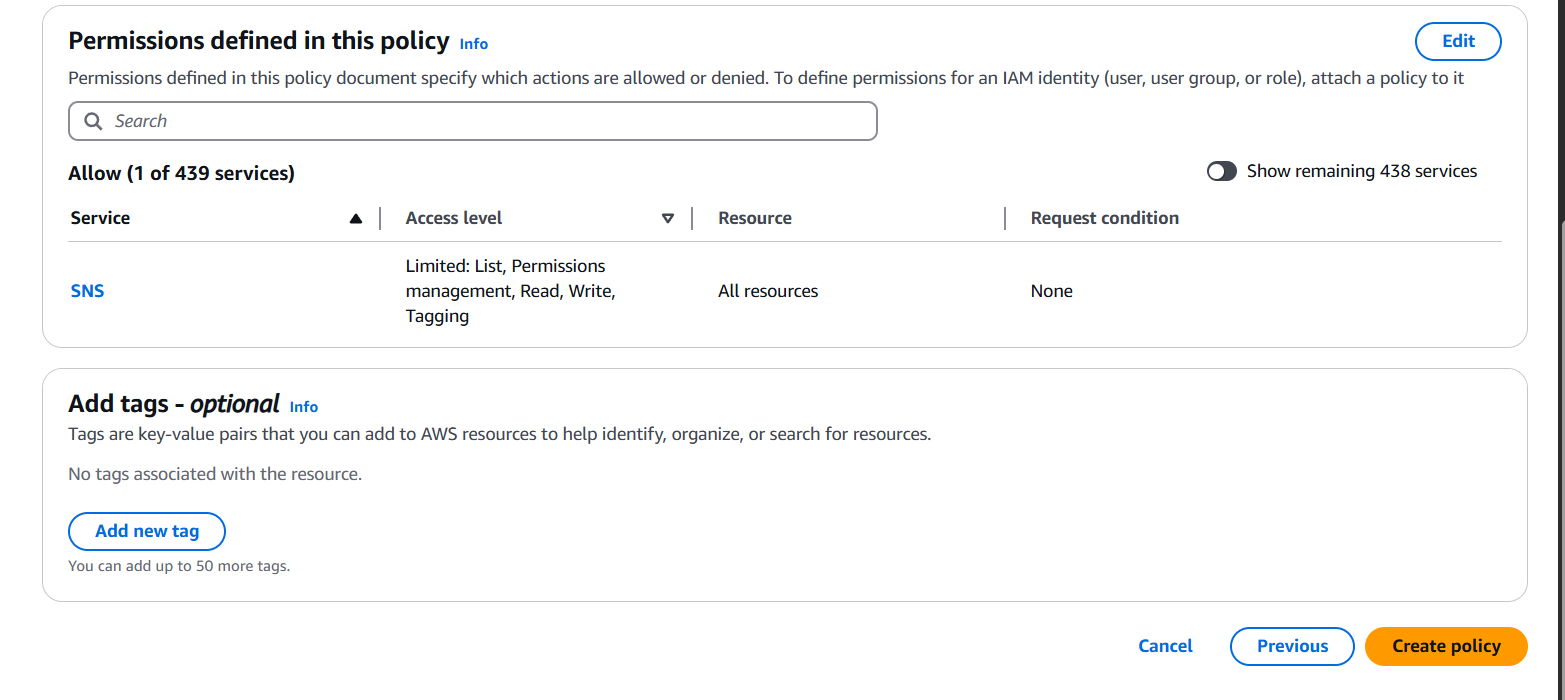
- Define the Service, Actions, and Resources.
- (Optional) Add conditions.
- Click Next: Tags, then Next: Review.
- Enter a name and description for the policy.
- Click Create policy.
Option 2: Using AWS CLI
aws iam create-policy \
--policy-name MyExamplePolicy \
--policy-document file://my-policy.json- Replace
my-policy.jsonwith the path to your JSON policy file.
✅ Basic IAM Policy Example (Read-Only Access to S3)
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:Get*",
"s3:List*"
],
"Resource": "*"
}
]
}This allows read-only access to all S3 buckets.

Conclusion.
Creating IAM policies in AWS might seem daunting at first, but with a solid understanding of their structure and purpose, it becomes a powerful skill that puts you in control of your cloud environment. By mastering the basics — from the policy JSON format to defining actions, resources, and conditions — you can design access controls that are both secure and precise. Whether you used the visual editor in the AWS Console or wrote policies manually with JSON, you’ve now taken a significant step toward managing permissions the right way.
IAM policies aren’t just about restricting access — they’re about giving the right people or services the right permissions at the right time. And when done correctly, they help enforce the principle of least privilege, minimize risk, and ensure compliance with organizational or regulatory standards.
As your AWS environment grows, so does the importance of getting IAM right. So keep practicing, review AWS documentation regularly, and explore more complex use cases like policy conditions, service control policies (SCPs), and permissions boundaries. The more comfortable you become with IAM, the better you’ll be at securing your infrastructure without slowing down development.
Thanks for reading — now go write those policies with confidence!

Add a Comment